Powershell is a shell for windows just like Bash is for unix, It is an excellent tool to automate tasks on windows machines but it also opens a lot of attack vectors like malicious scripts getting executed and hence microsoft decided to disable the auto execution of scripts and that means you need to type a few commands or mess with registry to enable quick execution of scripts.
There are four types of execution policies.
Execution Policy :
Restricted - Individual cmdlets can run, but not saved scripts. This is the default setting.
AllSigned - can run, but must have a digital signature even if written on the local computer. Prompts you before running scripts from trusted publishers.
RemoteSigned - Scripts written on the local computer do not need a digital signature, but any script downloaded from outside (email, IM, Internet) must have a signature to execute.
Unrestricted - Any script can run, but scripts downloaded from outside will run with a warning.
You can change the execution policy by editing the registry or the quickest is to do it from powershell itself.
To change it from registry go to
HKLMSOFTWAREMicrosoftPowerShell1ShellIdsMicrosoft.PowerShell. Find execution policy and type the policy which suits you.
Second one is to do it from powershell (recommended)
Type get-executionpolicy
then it will ask you for type of policy, type a policy suitable to you and press enter.
You are done, write as many scripts as you want and quickly run them.. ./crash
Friday, February 29, 2008
Enable execution OF Power Shell scripts
Powershell is a shell for windows just like Bash is for unix, It is an excellent tool to automate tasks on windows machines but it also opens a lot of attack vectors like malicious scripts getting executed and hence microsoft decided to disable the auto execution of scripts and that means you need to type a few commands or mess with registry to enable quick execution of scripts.
There are four types of execution policies.
Execution Policy :
Restricted - Individual cmdlets can run, but not saved scripts. This is the default setting.
AllSigned - can run, but must have a digital signature even if written on the local computer. Prompts you before running scripts from trusted publishers.
RemoteSigned - Scripts written on the local computer do not need a digital signature, but any script downloaded from outside (email, IM, Internet) must have a signature to execute.
Unrestricted - Any script can run, but scripts downloaded from outside will run with a warning.
You can change the execution policy by editing the registry or the quickest is to do it from powershell itself.
To change it from registry go to
HKLMSOFTWAREMicrosoftPowerShell1ShellIdsMicrosoft.PowerShell. Find execution policy and type the policy which suits you.
Second one is to do it from powershell (recommended)
Type get-executionpolicy
then it will ask you for type of policy, type a policy suitable to you and press enter.
You are done, write as many scripts as you want and quickly run them.. ./crash
There are four types of execution policies.
Execution Policy :
Restricted - Individual cmdlets can run, but not saved scripts. This is the default setting.
AllSigned - can run, but must have a digital signature even if written on the local computer. Prompts you before running scripts from trusted publishers.
RemoteSigned - Scripts written on the local computer do not need a digital signature, but any script downloaded from outside (email, IM, Internet) must have a signature to execute.
Unrestricted - Any script can run, but scripts downloaded from outside will run with a warning.
You can change the execution policy by editing the registry or the quickest is to do it from powershell itself.
To change it from registry go to
HKLMSOFTWAREMicrosoftPowerShell1ShellIdsMicrosoft.PowerShell. Find execution policy and type the policy which suits you.
Second one is to do it from powershell (recommended)
Type get-executionpolicy
then it will ask you for type of policy, type a policy suitable to you and press enter.
You are done, write as many scripts as you want and quickly run them.. ./crash
Enable execution OF Power Shell scripts
Powershell is a shell for windows just like Bash is for unix, It is an excellent tool to automate tasks on windows machines but it also opens a lot of attack vectors like malicious scripts getting executed and hence microsoft decided to disable the auto execution of scripts and that means you need to type a few commands or mess with registry to enable quick execution of scripts.
There are four types of execution policies.
Execution Policy :
Restricted - Individual cmdlets can run, but not saved scripts. This is the default setting.
AllSigned - can run, but must have a digital signature even if written on the local computer. Prompts you before running scripts from trusted publishers.
RemoteSigned - Scripts written on the local computer do not need a digital signature, but any script downloaded from outside (email, IM, Internet) must have a signature to execute.
Unrestricted - Any script can run, but scripts downloaded from outside will run with a warning.
You can change the execution policy by editing the registry or the quickest is to do it from powershell itself.
To change it from registry go to
HKLMSOFTWAREMicrosoftPowerShell1ShellIdsMicrosoft.PowerShell. Find execution policy and type the policy which suits you.
Second one is to do it from powershell (recommended)
Type get-executionpolicy
then it will ask you for type of policy, type a policy suitable to you and press enter.
You are done, write as many scripts as you want and quickly run them.. ./crash
There are four types of execution policies.
Execution Policy :
Restricted - Individual cmdlets can run, but not saved scripts. This is the default setting.
AllSigned - can run, but must have a digital signature even if written on the local computer. Prompts you before running scripts from trusted publishers.
RemoteSigned - Scripts written on the local computer do not need a digital signature, but any script downloaded from outside (email, IM, Internet) must have a signature to execute.
Unrestricted - Any script can run, but scripts downloaded from outside will run with a warning.
You can change the execution policy by editing the registry or the quickest is to do it from powershell itself.
To change it from registry go to
HKLMSOFTWAREMicrosoftPowerShell1ShellIdsMicrosoft.PowerShell. Find execution policy and type the policy which suits you.
Second one is to do it from powershell (recommended)
Type get-executionpolicy
then it will ask you for type of policy, type a policy suitable to you and press enter.
You are done, write as many scripts as you want and quickly run them.. ./crash
Enable execution OF Power Shell scripts
Powershell is a shell for windows just like Bash is for unix, It is an excellent tool to automate tasks on windows machines but it also opens a lot of attack vectors like malicious scripts getting executed and hence microsoft decided to disable the auto execution of scripts and that means you need to type a few commands or mess with registry to enable quick execution of scripts.
There are four types of execution policies.
Execution Policy :
Restricted - Individual cmdlets can run, but not saved scripts. This is the default setting.
AllSigned - can run, but must have a digital signature even if written on the local computer. Prompts you before running scripts from trusted publishers.
RemoteSigned - Scripts written on the local computer do not need a digital signature, but any script downloaded from outside (email, IM, Internet) must have a signature to execute.
Unrestricted - Any script can run, but scripts downloaded from outside will run with a warning.
You can change the execution policy by editing the registry or the quickest is to do it from powershell itself.
To change it from registry go to
HKLMSOFTWAREMicrosoftPowerShell1ShellIdsMicrosoft.PowerShell. Find execution policy and type the policy which suits you.
Second one is to do it from powershell (recommended)
Type get-executionpolicy
then it will ask you for type of policy, type a policy suitable to you and press enter.
You are done, write as many scripts as you want and quickly run them.. ./crash
There are four types of execution policies.
Execution Policy :
Restricted - Individual cmdlets can run, but not saved scripts. This is the default setting.
AllSigned - can run, but must have a digital signature even if written on the local computer. Prompts you before running scripts from trusted publishers.
RemoteSigned - Scripts written on the local computer do not need a digital signature, but any script downloaded from outside (email, IM, Internet) must have a signature to execute.
Unrestricted - Any script can run, but scripts downloaded from outside will run with a warning.
You can change the execution policy by editing the registry or the quickest is to do it from powershell itself.
To change it from registry go to
HKLMSOFTWAREMicrosoftPowerShell1ShellIdsMicrosoft.PowerShell. Find execution policy and type the policy which suits you.
Second one is to do it from powershell (recommended)
Type get-executionpolicy
then it will ask you for type of policy, type a policy suitable to you and press enter.
You are done, write as many scripts as you want and quickly run them.. ./crash
Enable execution OF Power Shell scripts
Powershell is a shell for windows just like Bash is for unix, It is an excellent tool to automate tasks on windows machines but it also opens a lot of attack vectors like malicious scripts getting executed and hence microsoft decided to disable the auto execution of scripts and that means you need to type a few commands or mess with registry to enable quick execution of scripts.
There are four types of execution policies.
Execution Policy :
Restricted - Individual cmdlets can run, but not saved scripts. This is the default setting.
AllSigned - can run, but must have a digital signature even if written on the local computer. Prompts you before running scripts from trusted publishers.
RemoteSigned - Scripts written on the local computer do not need a digital signature, but any script downloaded from outside (email, IM, Internet) must have a signature to execute.
Unrestricted - Any script can run, but scripts downloaded from outside will run with a warning.
You can change the execution policy by editing the registry or the quickest is to do it from powershell itself.
To change it from registry go to
HKLMSOFTWAREMicrosoftPowerShell1ShellIdsMicrosoft.PowerShell. Find execution policy and type the policy which suits you.
Second one is to do it from powershell (recommended)
Type get-executionpolicy
then it will ask you for type of policy, type a policy suitable to you and press enter.
You are done, write as many scripts as you want and quickly run them.. ./crash
There are four types of execution policies.
Execution Policy :
Restricted - Individual cmdlets can run, but not saved scripts. This is the default setting.
AllSigned - can run, but must have a digital signature even if written on the local computer. Prompts you before running scripts from trusted publishers.
RemoteSigned - Scripts written on the local computer do not need a digital signature, but any script downloaded from outside (email, IM, Internet) must have a signature to execute.
Unrestricted - Any script can run, but scripts downloaded from outside will run with a warning.
You can change the execution policy by editing the registry or the quickest is to do it from powershell itself.
To change it from registry go to
HKLMSOFTWAREMicrosoftPowerShell1ShellIdsMicrosoft.PowerShell. Find execution policy and type the policy which suits you.
Second one is to do it from powershell (recommended)
Type get-executionpolicy
then it will ask you for type of policy, type a policy suitable to you and press enter.
You are done, write as many scripts as you want and quickly run them.. ./crash
Enable execution OF Power Shell scripts
Powershell is a shell for windows just like Bash is for unix, It is an excellent tool to automate tasks on windows machines but it also opens a lot of attack vectors like malicious scripts getting executed and hence microsoft decided to disable the auto execution of scripts and that means you need to type a few commands or mess with registry to enable quick execution of scripts.
There are four types of execution policies.
Execution Policy :
Restricted - Individual cmdlets can run, but not saved scripts. This is the default setting.
AllSigned - can run, but must have a digital signature even if written on the local computer. Prompts you before running scripts from trusted publishers.
RemoteSigned - Scripts written on the local computer do not need a digital signature, but any script downloaded from outside (email, IM, Internet) must have a signature to execute.
Unrestricted - Any script can run, but scripts downloaded from outside will run with a warning.
You can change the execution policy by editing the registry or the quickest is to do it from powershell itself.
To change it from registry go to
HKLMSOFTWAREMicrosoftPowerShell1ShellIdsMicrosoft.PowerShell. Find execution policy and type the policy which suits you.
Second one is to do it from powershell (recommended)
Type get-executionpolicy
then it will ask you for type of policy, type a policy suitable to you and press enter.
You are done, write as many scripts as you want and quickly run them.. ./crash
There are four types of execution policies.
Execution Policy :
Restricted - Individual cmdlets can run, but not saved scripts. This is the default setting.
AllSigned - can run, but must have a digital signature even if written on the local computer. Prompts you before running scripts from trusted publishers.
RemoteSigned - Scripts written on the local computer do not need a digital signature, but any script downloaded from outside (email, IM, Internet) must have a signature to execute.
Unrestricted - Any script can run, but scripts downloaded from outside will run with a warning.
You can change the execution policy by editing the registry or the quickest is to do it from powershell itself.
To change it from registry go to
HKLMSOFTWAREMicrosoftPowerShell1ShellIdsMicrosoft.PowerShell. Find execution policy and type the policy which suits you.
Second one is to do it from powershell (recommended)
Type get-executionpolicy
then it will ask you for type of policy, type a policy suitable to you and press enter.
You are done, write as many scripts as you want and quickly run them.. ./crash
Enable execution OF Power Shell scripts
Powershell is a shell for windows just like Bash is for unix, It is an excellent tool to automate tasks on windows machines but it also opens a lot of attack vectors like malicious scripts getting executed and hence microsoft decided to disable the auto execution of scripts and that means you need to type a few commands or mess with registry to enable quick execution of scripts.
There are four types of execution policies.
Execution Policy :
Restricted - Individual cmdlets can run, but not saved scripts. This is the default setting.
AllSigned - can run, but must have a digital signature even if written on the local computer. Prompts you before running scripts from trusted publishers.
RemoteSigned - Scripts written on the local computer do not need a digital signature, but any script downloaded from outside (email, IM, Internet) must have a signature to execute.
Unrestricted - Any script can run, but scripts downloaded from outside will run with a warning.
You can change the execution policy by editing the registry or the quickest is to do it from powershell itself.
To change it from registry go to
HKLMSOFTWAREMicrosoftPowerShell1ShellIdsMicrosoft.PowerShell. Find execution policy and type the policy which suits you.
Second one is to do it from powershell (recommended)
Type get-executionpolicy
then it will ask you for type of policy, type a policy suitable to you and press enter.
You are done, write as many scripts as you want and quickly run them.. ./crash
There are four types of execution policies.
Execution Policy :
Restricted - Individual cmdlets can run, but not saved scripts. This is the default setting.
AllSigned - can run, but must have a digital signature even if written on the local computer. Prompts you before running scripts from trusted publishers.
RemoteSigned - Scripts written on the local computer do not need a digital signature, but any script downloaded from outside (email, IM, Internet) must have a signature to execute.
Unrestricted - Any script can run, but scripts downloaded from outside will run with a warning.
You can change the execution policy by editing the registry or the quickest is to do it from powershell itself.
To change it from registry go to
HKLMSOFTWAREMicrosoftPowerShell1ShellIdsMicrosoft.PowerShell. Find execution policy and type the policy which suits you.
Second one is to do it from powershell (recommended)
Type get-executionpolicy
then it will ask you for type of policy, type a policy suitable to you and press enter.
You are done, write as many scripts as you want and quickly run them.. ./crash
Enable execution OF Power Shell scripts
Powershell is a shell for windows just like Bash is for unix, It is an excellent tool to automate tasks on windows machines but it also opens a lot of attack vectors like malicious scripts getting executed and hence microsoft decided to disable the auto execution of scripts and that means you need to type a few commands or mess with registry to enable quick execution of scripts.
There are four types of execution policies.
Execution Policy :
Restricted - Individual cmdlets can run, but not saved scripts. This is the default setting.
AllSigned - can run, but must have a digital signature even if written on the local computer. Prompts you before running scripts from trusted publishers.
RemoteSigned - Scripts written on the local computer do not need a digital signature, but any script downloaded from outside (email, IM, Internet) must have a signature to execute.
Unrestricted - Any script can run, but scripts downloaded from outside will run with a warning.
You can change the execution policy by editing the registry or the quickest is to do it from powershell itself.
To change it from registry go to
HKLMSOFTWAREMicrosoftPowerShell1ShellIdsMicrosoft.PowerShell. Find execution policy and type the policy which suits you.
Second one is to do it from powershell (recommended)
Type get-executionpolicy
then it will ask you for type of policy, type a policy suitable to you and press enter.
You are done, write as many scripts as you want and quickly run them.. ./crash
There are four types of execution policies.
Execution Policy :
Restricted - Individual cmdlets can run, but not saved scripts. This is the default setting.
AllSigned - can run, but must have a digital signature even if written on the local computer. Prompts you before running scripts from trusted publishers.
RemoteSigned - Scripts written on the local computer do not need a digital signature, but any script downloaded from outside (email, IM, Internet) must have a signature to execute.
Unrestricted - Any script can run, but scripts downloaded from outside will run with a warning.
You can change the execution policy by editing the registry or the quickest is to do it from powershell itself.
To change it from registry go to
HKLMSOFTWAREMicrosoftPowerShell1ShellIdsMicrosoft.PowerShell. Find execution policy and type the policy which suits you.
Second one is to do it from powershell (recommended)
Type get-executionpolicy
then it will ask you for type of policy, type a policy suitable to you and press enter.
You are done, write as many scripts as you want and quickly run them.. ./crash
Enable execution OF Power Shell scripts
Powershell is a shell for windows just like Bash is for unix, It is an excellent tool to automate tasks on windows machines but it also opens a lot of attack vectors like malicious scripts getting executed and hence microsoft decided to disable the auto execution of scripts and that means you need to type a few commands or mess with registry to enable quick execution of scripts.
There are four types of execution policies.
Execution Policy :
Restricted - Individual cmdlets can run, but not saved scripts. This is the default setting.
AllSigned - can run, but must have a digital signature even if written on the local computer. Prompts you before running scripts from trusted publishers.
RemoteSigned - Scripts written on the local computer do not need a digital signature, but any script downloaded from outside (email, IM, Internet) must have a signature to execute.
Unrestricted - Any script can run, but scripts downloaded from outside will run with a warning.
You can change the execution policy by editing the registry or the quickest is to do it from powershell itself.
To change it from registry go to
HKLMSOFTWAREMicrosoftPowerShell1ShellIdsMicrosoft.PowerShell. Find execution policy and type the policy which suits you.
Second one is to do it from powershell (recommended)
Type get-executionpolicy
then it will ask you for type of policy, type a policy suitable to you and press enter.
You are done, write as many scripts as you want and quickly run them.. ./crash
There are four types of execution policies.
Execution Policy :
Restricted - Individual cmdlets can run, but not saved scripts. This is the default setting.
AllSigned - can run, but must have a digital signature even if written on the local computer. Prompts you before running scripts from trusted publishers.
RemoteSigned - Scripts written on the local computer do not need a digital signature, but any script downloaded from outside (email, IM, Internet) must have a signature to execute.
Unrestricted - Any script can run, but scripts downloaded from outside will run with a warning.
You can change the execution policy by editing the registry or the quickest is to do it from powershell itself.
To change it from registry go to
HKLMSOFTWAREMicrosoftPowerShell1ShellIdsMicrosoft.PowerShell. Find execution policy and type the policy which suits you.
Second one is to do it from powershell (recommended)
Type get-executionpolicy
then it will ask you for type of policy, type a policy suitable to you and press enter.
You are done, write as many scripts as you want and quickly run them.. ./crash
Enable execution OF Power Shell scripts
Powershell is a shell for windows just like Bash is for unix, It is an excellent tool to automate tasks on windows machines but it also opens a lot of attack vectors like malicious scripts getting executed and hence microsoft decided to disable the auto execution of scripts and that means you need to type a few commands or mess with registry to enable quick execution of scripts.
There are four types of execution policies.
Execution Policy :
Restricted - Individual cmdlets can run, but not saved scripts. This is the default setting.
AllSigned - can run, but must have a digital signature even if written on the local computer. Prompts you before running scripts from trusted publishers.
RemoteSigned - Scripts written on the local computer do not need a digital signature, but any script downloaded from outside (email, IM, Internet) must have a signature to execute.
Unrestricted - Any script can run, but scripts downloaded from outside will run with a warning.
You can change the execution policy by editing the registry or the quickest is to do it from powershell itself.
To change it from registry go to
HKLMSOFTWAREMicrosoftPowerShell1ShellIdsMicrosoft.PowerShell. Find execution policy and type the policy which suits you.
Second one is to do it from powershell (recommended)
Type get-executionpolicy
then it will ask you for type of policy, type a policy suitable to you and press enter.
You are done, write as many scripts as you want and quickly run them.. ./crash
There are four types of execution policies.
Execution Policy :
Restricted - Individual cmdlets can run, but not saved scripts. This is the default setting.
AllSigned - can run, but must have a digital signature even if written on the local computer. Prompts you before running scripts from trusted publishers.
RemoteSigned - Scripts written on the local computer do not need a digital signature, but any script downloaded from outside (email, IM, Internet) must have a signature to execute.
Unrestricted - Any script can run, but scripts downloaded from outside will run with a warning.
You can change the execution policy by editing the registry or the quickest is to do it from powershell itself.
To change it from registry go to
HKLMSOFTWAREMicrosoftPowerShell1ShellIdsMicrosoft.PowerShell. Find execution policy and type the policy which suits you.
Second one is to do it from powershell (recommended)
Type get-executionpolicy
then it will ask you for type of policy, type a policy suitable to you and press enter.
You are done, write as many scripts as you want and quickly run them.. ./crash
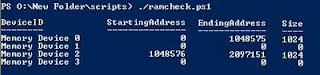
You can check the amount of RAM on your windows box and can verify if any more slots are availiable or not if you want to add more RAM.
Use this code to check the RAM and Memory slot status:
$computer = "."
gwmi -co $computer -class win32_memorydevice | `
ft -prop DeviceID,StartingAddress,EndingAddress, `
@{
Label="Size";
Expression={[math]::round(($_.EndingAddress - $_.StartingAddress)/1024,0)}
}
You can save this code into a file with a .ps1 extension like ramcheck.ps1
Now execute it with ./ramcheck.ps1
With this example you can see that this machine has 2 GB of RAM in 2 slots no.1 and no.3 and both RAM chips have the size of 1GB each.
StartingAddress and EndingAddress helps you to determine the size of chip in the memory slot.
--Abhiz

You can check the amount of RAM on your windows box and can verify if any more slots are availiable or not if you want to add more RAM.
Use this code to check the RAM and Memory slot status:
$computer = "."
gwmi -co $computer -class win32_memorydevice | `
ft -prop DeviceID,StartingAddress,EndingAddress, `
@{
Label="Size";
Expression={[math]::round(($_.EndingAddress - $_.StartingAddress)/1024,0)}
}
You can save this code into a file with a .ps1 extension like ramcheck.ps1
Now execute it with ./ramcheck.ps1
With this example you can see that this machine has 2 GB of RAM in 2 slots no.1 and no.3 and both RAM chips have the size of 1GB each.
StartingAddress and EndingAddress helps you to determine the size of chip in the memory slot.
--Abhiz

You can check the amount of RAM on your windows box and can verify if any more slots are availiable or not if you want to add more RAM.
Use this code to check the RAM and Memory slot status:
$computer = "."
gwmi -co $computer -class win32_memorydevice | `
ft -prop DeviceID,StartingAddress,EndingAddress, `
@{
Label="Size";
Expression={[math]::round(($_.EndingAddress - $_.StartingAddress)/1024,0)}
}
You can save this code into a file with a .ps1 extension like ramcheck.ps1
Now execute it with ./ramcheck.ps1
With this example you can see that this machine has 2 GB of RAM in 2 slots no.1 and no.3 and both RAM chips have the size of 1GB each.
StartingAddress and EndingAddress helps you to determine the size of chip in the memory slot.
--Abhiz

You can check the amount of RAM on your windows box and can verify if any more slots are availiable or not if you want to add more RAM.
Use this code to check the RAM and Memory slot status:
$computer = "."
gwmi -co $computer -class win32_memorydevice | `
ft -prop DeviceID,StartingAddress,EndingAddress, `
@{
Label="Size";
Expression={[math]::round(($_.EndingAddress - $_.StartingAddress)/1024,0)}
}
You can save this code into a file with a .ps1 extension like ramcheck.ps1
Now execute it with ./ramcheck.ps1
With this example you can see that this machine has 2 GB of RAM in 2 slots no.1 and no.3 and both RAM chips have the size of 1GB each.
StartingAddress and EndingAddress helps you to determine the size of chip in the memory slot.
--Abhiz

You can check the amount of RAM on your windows box and can verify if any more slots are availiable or not if you want to add more RAM.
Use this code to check the RAM and Memory slot status:
$computer = "."
gwmi -co $computer -class win32_memorydevice | `
ft -prop DeviceID,StartingAddress,EndingAddress, `
@{
Label="Size";
Expression={[math]::round(($_.EndingAddress - $_.StartingAddress)/1024,0)}
}
You can save this code into a file with a .ps1 extension like ramcheck.ps1
Now execute it with ./ramcheck.ps1
With this example you can see that this machine has 2 GB of RAM in 2 slots no.1 and no.3 and both RAM chips have the size of 1GB each.
StartingAddress and EndingAddress helps you to determine the size of chip in the memory slot.
--Abhiz

You can check the amount of RAM on your windows box and can verify if any more slots are availiable or not if you want to add more RAM.
Use this code to check the RAM and Memory slot status:
$computer = "."
gwmi -co $computer -class win32_memorydevice | `
ft -prop DeviceID,StartingAddress,EndingAddress, `
@{
Label="Size";
Expression={[math]::round(($_.EndingAddress - $_.StartingAddress)/1024,0)}
}
You can save this code into a file with a .ps1 extension like ramcheck.ps1
Now execute it with ./ramcheck.ps1
With this example you can see that this machine has 2 GB of RAM in 2 slots no.1 and no.3 and both RAM chips have the size of 1GB each.
StartingAddress and EndingAddress helps you to determine the size of chip in the memory slot.
--Abhiz

You can check the amount of RAM on your windows box and can verify if any more slots are availiable or not if you want to add more RAM.
Use this code to check the RAM and Memory slot status:
$computer = "."
gwmi -co $computer -class win32_memorydevice | `
ft -prop DeviceID,StartingAddress,EndingAddress, `
@{
Label="Size";
Expression={[math]::round(($_.EndingAddress - $_.StartingAddress)/1024,0)}
}
You can save this code into a file with a .ps1 extension like ramcheck.ps1
Now execute it with ./ramcheck.ps1
With this example you can see that this machine has 2 GB of RAM in 2 slots no.1 and no.3 and both RAM chips have the size of 1GB each.
StartingAddress and EndingAddress helps you to determine the size of chip in the memory slot.
--Abhiz

You can check the amount of RAM on your windows box and can verify if any more slots are availiable or not if you want to add more RAM.
Use this code to check the RAM and Memory slot status:
$computer = "."
gwmi -co $computer -class win32_memorydevice | `
ft -prop DeviceID,StartingAddress,EndingAddress, `
@{
Label="Size";
Expression={[math]::round(($_.EndingAddress - $_.StartingAddress)/1024,0)}
}
You can save this code into a file with a .ps1 extension like ramcheck.ps1
Now execute it with ./ramcheck.ps1
With this example you can see that this machine has 2 GB of RAM in 2 slots no.1 and no.3 and both RAM chips have the size of 1GB each.
StartingAddress and EndingAddress helps you to determine the size of chip in the memory slot.
--Abhiz

You can check the amount of RAM on your windows box and can verify if any more slots are availiable or not if you want to add more RAM.
Use this code to check the RAM and Memory slot status:
$computer = "."
gwmi -co $computer -class win32_memorydevice | `
ft -prop DeviceID,StartingAddress,EndingAddress, `
@{
Label="Size";
Expression={[math]::round(($_.EndingAddress - $_.StartingAddress)/1024,0)}
}
You can save this code into a file with a .ps1 extension like ramcheck.ps1
Now execute it with ./ramcheck.ps1
With this example you can see that this machine has 2 GB of RAM in 2 slots no.1 and no.3 and both RAM chips have the size of 1GB each.
StartingAddress and EndingAddress helps you to determine the size of chip in the memory slot.
--Abhiz

You can check the amount of RAM on your windows box and can verify if any more slots are availiable or not if you want to add more RAM.
Use this code to check the RAM and Memory slot status:
$computer = "."
gwmi -co $computer -class win32_memorydevice | `
ft -prop DeviceID,StartingAddress,EndingAddress, `
@{
Label="Size";
Expression={[math]::round(($_.EndingAddress - $_.StartingAddress)/1024,0)}
}
You can save this code into a file with a .ps1 extension like ramcheck.ps1
Now execute it with ./ramcheck.ps1
With this example you can see that this machine has 2 GB of RAM in 2 slots no.1 and no.3 and both RAM chips have the size of 1GB each.
StartingAddress and EndingAddress helps you to determine the size of chip in the memory slot.
--Abhiz
TrendMicro releases Blackhat pricing
Trend Micro has released its 2007 Annual Roundup and 2008 Forecast. The report contains a few interesting points that could be new compared to other reports.
The report talks about the growth of web threats, which increased yearly up to 2006 but seems to have slowed down over the last twelve months. They also notice a significant increase in the number of attacks on smart phones and other mobile gadgets. Take it with a grain of salt.
However, the most interesting part of the report is the pricing chart for black hat services:
adware from 2 to 20 cents per installation depending on location
exploit kit rental around $1 per hour
access to installed information stealing trojans around $80 each
DDoS around $100 per day
individual banking credentials from $50
Other notable findings from the report:
- The Windows Animated Cursor exploit (EXPL_ANICMOO) encompassed over 50 percent of all exploit codes to hit the Internet computing population. 74 percent of its infections this year came from Asia. The same holds true for TROJ_ANICMOO.AX, a related threat which embedded the exploit. 64 percent of computers infected with this were from China.
- The top malware finding was WORM_SPYBOT.IS and WORM_GAOBOT.DF. Both created botnets and worms that infected USB-connected devices.
- Nearly 50 percent of all threat infections come from North America, but Asian countries are also experiencing a growth -- 40 percent of infections stem from that region.
-Social networking communities and user-created content such as blog sites became infection vectors due to attacks on their underlying Web 2.0 technologies, particularly cross-site scripting and streaming technologies.
- Infection volumes nearly quadrupled between September and November 2007, indicating that malware authors took advantage of the holiday seasons as an opportunity to send spam or deploy spyware while users are shopping online.
- In 2007, the top online commerce site attacked by phishers was still global auction site eBay and sister company PayPal. Financial institutions, especially those based in North America, also experienced a high volume of phising attacks.
2008 Forecast
Based on the emerging trends of this year, the following are Trend Micro’s forecasts for the 2008 threat landscape:
1. Legacy code used in operating systems and vulnerabilities in popular applications will continue to be attacked in the effort to inject in-process malicious code that criminals can exploit to run malware as they attempt to steal confidential and proprietary information.
2. High-profile Web sites that run the gamut of social networking, banking/financial, online gaming, search engine, travel, commercial ticketing, local government sectors, news, job, blogging, and e-commerce sites for auction and shopping will continue to be the most sought-after attack vectors by criminals to host links to phishing and identity theft code.
3. Unmanaged devices such as smart phones, mp3 players, digital frames, thumb drives and gaming stations will continue to provide opportunities for criminals and malware to infiltrate a company’s security borders due to their capabilities for storage, computing and Wi-Fi. Public access points such as those in coffee shops, bookstores, hotel lobbies, and airports will continue to be distribution points for malware or attack vectors used by malicious entities.
4. Communication services such as email, instant messaging, as well as file sharing will continue to be abused by content threats such as image spam, malicious URLs and attachments via targeted and localized social engineered themes.
5. Data protection and software security strategies will become standard in the commercial software lifecycle. This will also put a focus on data encryption technologies during storage and transit particularly in the vetting of data access in the information and distribution chain.
--Abhiz
The report talks about the growth of web threats, which increased yearly up to 2006 but seems to have slowed down over the last twelve months. They also notice a significant increase in the number of attacks on smart phones and other mobile gadgets. Take it with a grain of salt.
However, the most interesting part of the report is the pricing chart for black hat services:
adware from 2 to 20 cents per installation depending on location
exploit kit rental around $1 per hour
access to installed information stealing trojans around $80 each
DDoS around $100 per day
individual banking credentials from $50
Other notable findings from the report:
- The Windows Animated Cursor exploit (EXPL_ANICMOO) encompassed over 50 percent of all exploit codes to hit the Internet computing population. 74 percent of its infections this year came from Asia. The same holds true for TROJ_ANICMOO.AX, a related threat which embedded the exploit. 64 percent of computers infected with this were from China.
- The top malware finding was WORM_SPYBOT.IS and WORM_GAOBOT.DF. Both created botnets and worms that infected USB-connected devices.
- Nearly 50 percent of all threat infections come from North America, but Asian countries are also experiencing a growth -- 40 percent of infections stem from that region.
-Social networking communities and user-created content such as blog sites became infection vectors due to attacks on their underlying Web 2.0 technologies, particularly cross-site scripting and streaming technologies.
- Infection volumes nearly quadrupled between September and November 2007, indicating that malware authors took advantage of the holiday seasons as an opportunity to send spam or deploy spyware while users are shopping online.
- In 2007, the top online commerce site attacked by phishers was still global auction site eBay and sister company PayPal. Financial institutions, especially those based in North America, also experienced a high volume of phising attacks.
2008 Forecast
Based on the emerging trends of this year, the following are Trend Micro’s forecasts for the 2008 threat landscape:
1. Legacy code used in operating systems and vulnerabilities in popular applications will continue to be attacked in the effort to inject in-process malicious code that criminals can exploit to run malware as they attempt to steal confidential and proprietary information.
2. High-profile Web sites that run the gamut of social networking, banking/financial, online gaming, search engine, travel, commercial ticketing, local government sectors, news, job, blogging, and e-commerce sites for auction and shopping will continue to be the most sought-after attack vectors by criminals to host links to phishing and identity theft code.
3. Unmanaged devices such as smart phones, mp3 players, digital frames, thumb drives and gaming stations will continue to provide opportunities for criminals and malware to infiltrate a company’s security borders due to their capabilities for storage, computing and Wi-Fi. Public access points such as those in coffee shops, bookstores, hotel lobbies, and airports will continue to be distribution points for malware or attack vectors used by malicious entities.
4. Communication services such as email, instant messaging, as well as file sharing will continue to be abused by content threats such as image spam, malicious URLs and attachments via targeted and localized social engineered themes.
5. Data protection and software security strategies will become standard in the commercial software lifecycle. This will also put a focus on data encryption technologies during storage and transit particularly in the vetting of data access in the information and distribution chain.
--Abhiz
TrendMicro releases Blackhat pricing
Trend Micro has released its 2007 Annual Roundup and 2008 Forecast. The report contains a few interesting points that could be new compared to other reports.
The report talks about the growth of web threats, which increased yearly up to 2006 but seems to have slowed down over the last twelve months. They also notice a significant increase in the number of attacks on smart phones and other mobile gadgets. Take it with a grain of salt.
However, the most interesting part of the report is the pricing chart for black hat services:
adware from 2 to 20 cents per installation depending on location
exploit kit rental around $1 per hour
access to installed information stealing trojans around $80 each
DDoS around $100 per day
individual banking credentials from $50
Other notable findings from the report:
- The Windows Animated Cursor exploit (EXPL_ANICMOO) encompassed over 50 percent of all exploit codes to hit the Internet computing population. 74 percent of its infections this year came from Asia. The same holds true for TROJ_ANICMOO.AX, a related threat which embedded the exploit. 64 percent of computers infected with this were from China.
- The top malware finding was WORM_SPYBOT.IS and WORM_GAOBOT.DF. Both created botnets and worms that infected USB-connected devices.
- Nearly 50 percent of all threat infections come from North America, but Asian countries are also experiencing a growth -- 40 percent of infections stem from that region.
-Social networking communities and user-created content such as blog sites became infection vectors due to attacks on their underlying Web 2.0 technologies, particularly cross-site scripting and streaming technologies.
- Infection volumes nearly quadrupled between September and November 2007, indicating that malware authors took advantage of the holiday seasons as an opportunity to send spam or deploy spyware while users are shopping online.
- In 2007, the top online commerce site attacked by phishers was still global auction site eBay and sister company PayPal. Financial institutions, especially those based in North America, also experienced a high volume of phising attacks.
2008 Forecast
Based on the emerging trends of this year, the following are Trend Micro’s forecasts for the 2008 threat landscape:
1. Legacy code used in operating systems and vulnerabilities in popular applications will continue to be attacked in the effort to inject in-process malicious code that criminals can exploit to run malware as they attempt to steal confidential and proprietary information.
2. High-profile Web sites that run the gamut of social networking, banking/financial, online gaming, search engine, travel, commercial ticketing, local government sectors, news, job, blogging, and e-commerce sites for auction and shopping will continue to be the most sought-after attack vectors by criminals to host links to phishing and identity theft code.
3. Unmanaged devices such as smart phones, mp3 players, digital frames, thumb drives and gaming stations will continue to provide opportunities for criminals and malware to infiltrate a company’s security borders due to their capabilities for storage, computing and Wi-Fi. Public access points such as those in coffee shops, bookstores, hotel lobbies, and airports will continue to be distribution points for malware or attack vectors used by malicious entities.
4. Communication services such as email, instant messaging, as well as file sharing will continue to be abused by content threats such as image spam, malicious URLs and attachments via targeted and localized social engineered themes.
5. Data protection and software security strategies will become standard in the commercial software lifecycle. This will also put a focus on data encryption technologies during storage and transit particularly in the vetting of data access in the information and distribution chain.
--Abhiz
The report talks about the growth of web threats, which increased yearly up to 2006 but seems to have slowed down over the last twelve months. They also notice a significant increase in the number of attacks on smart phones and other mobile gadgets. Take it with a grain of salt.
However, the most interesting part of the report is the pricing chart for black hat services:
adware from 2 to 20 cents per installation depending on location
exploit kit rental around $1 per hour
access to installed information stealing trojans around $80 each
DDoS around $100 per day
individual banking credentials from $50
Other notable findings from the report:
- The Windows Animated Cursor exploit (EXPL_ANICMOO) encompassed over 50 percent of all exploit codes to hit the Internet computing population. 74 percent of its infections this year came from Asia. The same holds true for TROJ_ANICMOO.AX, a related threat which embedded the exploit. 64 percent of computers infected with this were from China.
- The top malware finding was WORM_SPYBOT.IS and WORM_GAOBOT.DF. Both created botnets and worms that infected USB-connected devices.
- Nearly 50 percent of all threat infections come from North America, but Asian countries are also experiencing a growth -- 40 percent of infections stem from that region.
-Social networking communities and user-created content such as blog sites became infection vectors due to attacks on their underlying Web 2.0 technologies, particularly cross-site scripting and streaming technologies.
- Infection volumes nearly quadrupled between September and November 2007, indicating that malware authors took advantage of the holiday seasons as an opportunity to send spam or deploy spyware while users are shopping online.
- In 2007, the top online commerce site attacked by phishers was still global auction site eBay and sister company PayPal. Financial institutions, especially those based in North America, also experienced a high volume of phising attacks.
2008 Forecast
Based on the emerging trends of this year, the following are Trend Micro’s forecasts for the 2008 threat landscape:
1. Legacy code used in operating systems and vulnerabilities in popular applications will continue to be attacked in the effort to inject in-process malicious code that criminals can exploit to run malware as they attempt to steal confidential and proprietary information.
2. High-profile Web sites that run the gamut of social networking, banking/financial, online gaming, search engine, travel, commercial ticketing, local government sectors, news, job, blogging, and e-commerce sites for auction and shopping will continue to be the most sought-after attack vectors by criminals to host links to phishing and identity theft code.
3. Unmanaged devices such as smart phones, mp3 players, digital frames, thumb drives and gaming stations will continue to provide opportunities for criminals and malware to infiltrate a company’s security borders due to their capabilities for storage, computing and Wi-Fi. Public access points such as those in coffee shops, bookstores, hotel lobbies, and airports will continue to be distribution points for malware or attack vectors used by malicious entities.
4. Communication services such as email, instant messaging, as well as file sharing will continue to be abused by content threats such as image spam, malicious URLs and attachments via targeted and localized social engineered themes.
5. Data protection and software security strategies will become standard in the commercial software lifecycle. This will also put a focus on data encryption technologies during storage and transit particularly in the vetting of data access in the information and distribution chain.
--Abhiz
TrendMicro releases Blackhat pricing
Trend Micro has released its 2007 Annual Roundup and 2008 Forecast. The report contains a few interesting points that could be new compared to other reports.
The report talks about the growth of web threats, which increased yearly up to 2006 but seems to have slowed down over the last twelve months. They also notice a significant increase in the number of attacks on smart phones and other mobile gadgets. Take it with a grain of salt.
However, the most interesting part of the report is the pricing chart for black hat services:
adware from 2 to 20 cents per installation depending on location
exploit kit rental around $1 per hour
access to installed information stealing trojans around $80 each
DDoS around $100 per day
individual banking credentials from $50
Other notable findings from the report:
- The Windows Animated Cursor exploit (EXPL_ANICMOO) encompassed over 50 percent of all exploit codes to hit the Internet computing population. 74 percent of its infections this year came from Asia. The same holds true for TROJ_ANICMOO.AX, a related threat which embedded the exploit. 64 percent of computers infected with this were from China.
- The top malware finding was WORM_SPYBOT.IS and WORM_GAOBOT.DF. Both created botnets and worms that infected USB-connected devices.
- Nearly 50 percent of all threat infections come from North America, but Asian countries are also experiencing a growth -- 40 percent of infections stem from that region.
-Social networking communities and user-created content such as blog sites became infection vectors due to attacks on their underlying Web 2.0 technologies, particularly cross-site scripting and streaming technologies.
- Infection volumes nearly quadrupled between September and November 2007, indicating that malware authors took advantage of the holiday seasons as an opportunity to send spam or deploy spyware while users are shopping online.
- In 2007, the top online commerce site attacked by phishers was still global auction site eBay and sister company PayPal. Financial institutions, especially those based in North America, also experienced a high volume of phising attacks.
2008 Forecast
Based on the emerging trends of this year, the following are Trend Micro’s forecasts for the 2008 threat landscape:
1. Legacy code used in operating systems and vulnerabilities in popular applications will continue to be attacked in the effort to inject in-process malicious code that criminals can exploit to run malware as they attempt to steal confidential and proprietary information.
2. High-profile Web sites that run the gamut of social networking, banking/financial, online gaming, search engine, travel, commercial ticketing, local government sectors, news, job, blogging, and e-commerce sites for auction and shopping will continue to be the most sought-after attack vectors by criminals to host links to phishing and identity theft code.
3. Unmanaged devices such as smart phones, mp3 players, digital frames, thumb drives and gaming stations will continue to provide opportunities for criminals and malware to infiltrate a company’s security borders due to their capabilities for storage, computing and Wi-Fi. Public access points such as those in coffee shops, bookstores, hotel lobbies, and airports will continue to be distribution points for malware or attack vectors used by malicious entities.
4. Communication services such as email, instant messaging, as well as file sharing will continue to be abused by content threats such as image spam, malicious URLs and attachments via targeted and localized social engineered themes.
5. Data protection and software security strategies will become standard in the commercial software lifecycle. This will also put a focus on data encryption technologies during storage and transit particularly in the vetting of data access in the information and distribution chain.
--Abhiz
The report talks about the growth of web threats, which increased yearly up to 2006 but seems to have slowed down over the last twelve months. They also notice a significant increase in the number of attacks on smart phones and other mobile gadgets. Take it with a grain of salt.
However, the most interesting part of the report is the pricing chart for black hat services:
adware from 2 to 20 cents per installation depending on location
exploit kit rental around $1 per hour
access to installed information stealing trojans around $80 each
DDoS around $100 per day
individual banking credentials from $50
Other notable findings from the report:
- The Windows Animated Cursor exploit (EXPL_ANICMOO) encompassed over 50 percent of all exploit codes to hit the Internet computing population. 74 percent of its infections this year came from Asia. The same holds true for TROJ_ANICMOO.AX, a related threat which embedded the exploit. 64 percent of computers infected with this were from China.
- The top malware finding was WORM_SPYBOT.IS and WORM_GAOBOT.DF. Both created botnets and worms that infected USB-connected devices.
- Nearly 50 percent of all threat infections come from North America, but Asian countries are also experiencing a growth -- 40 percent of infections stem from that region.
-Social networking communities and user-created content such as blog sites became infection vectors due to attacks on their underlying Web 2.0 technologies, particularly cross-site scripting and streaming technologies.
- Infection volumes nearly quadrupled between September and November 2007, indicating that malware authors took advantage of the holiday seasons as an opportunity to send spam or deploy spyware while users are shopping online.
- In 2007, the top online commerce site attacked by phishers was still global auction site eBay and sister company PayPal. Financial institutions, especially those based in North America, also experienced a high volume of phising attacks.
2008 Forecast
Based on the emerging trends of this year, the following are Trend Micro’s forecasts for the 2008 threat landscape:
1. Legacy code used in operating systems and vulnerabilities in popular applications will continue to be attacked in the effort to inject in-process malicious code that criminals can exploit to run malware as they attempt to steal confidential and proprietary information.
2. High-profile Web sites that run the gamut of social networking, banking/financial, online gaming, search engine, travel, commercial ticketing, local government sectors, news, job, blogging, and e-commerce sites for auction and shopping will continue to be the most sought-after attack vectors by criminals to host links to phishing and identity theft code.
3. Unmanaged devices such as smart phones, mp3 players, digital frames, thumb drives and gaming stations will continue to provide opportunities for criminals and malware to infiltrate a company’s security borders due to their capabilities for storage, computing and Wi-Fi. Public access points such as those in coffee shops, bookstores, hotel lobbies, and airports will continue to be distribution points for malware or attack vectors used by malicious entities.
4. Communication services such as email, instant messaging, as well as file sharing will continue to be abused by content threats such as image spam, malicious URLs and attachments via targeted and localized social engineered themes.
5. Data protection and software security strategies will become standard in the commercial software lifecycle. This will also put a focus on data encryption technologies during storage and transit particularly in the vetting of data access in the information and distribution chain.
--Abhiz
TrendMicro releases Blackhat pricing
Trend Micro has released its 2007 Annual Roundup and 2008 Forecast. The report contains a few interesting points that could be new compared to other reports.
The report talks about the growth of web threats, which increased yearly up to 2006 but seems to have slowed down over the last twelve months. They also notice a significant increase in the number of attacks on smart phones and other mobile gadgets. Take it with a grain of salt.
However, the most interesting part of the report is the pricing chart for black hat services:
adware from 2 to 20 cents per installation depending on location
exploit kit rental around $1 per hour
access to installed information stealing trojans around $80 each
DDoS around $100 per day
individual banking credentials from $50
Other notable findings from the report:
- The Windows Animated Cursor exploit (EXPL_ANICMOO) encompassed over 50 percent of all exploit codes to hit the Internet computing population. 74 percent of its infections this year came from Asia. The same holds true for TROJ_ANICMOO.AX, a related threat which embedded the exploit. 64 percent of computers infected with this were from China.
- The top malware finding was WORM_SPYBOT.IS and WORM_GAOBOT.DF. Both created botnets and worms that infected USB-connected devices.
- Nearly 50 percent of all threat infections come from North America, but Asian countries are also experiencing a growth -- 40 percent of infections stem from that region.
-Social networking communities and user-created content such as blog sites became infection vectors due to attacks on their underlying Web 2.0 technologies, particularly cross-site scripting and streaming technologies.
- Infection volumes nearly quadrupled between September and November 2007, indicating that malware authors took advantage of the holiday seasons as an opportunity to send spam or deploy spyware while users are shopping online.
- In 2007, the top online commerce site attacked by phishers was still global auction site eBay and sister company PayPal. Financial institutions, especially those based in North America, also experienced a high volume of phising attacks.
2008 Forecast
Based on the emerging trends of this year, the following are Trend Micro’s forecasts for the 2008 threat landscape:
1. Legacy code used in operating systems and vulnerabilities in popular applications will continue to be attacked in the effort to inject in-process malicious code that criminals can exploit to run malware as they attempt to steal confidential and proprietary information.
2. High-profile Web sites that run the gamut of social networking, banking/financial, online gaming, search engine, travel, commercial ticketing, local government sectors, news, job, blogging, and e-commerce sites for auction and shopping will continue to be the most sought-after attack vectors by criminals to host links to phishing and identity theft code.
3. Unmanaged devices such as smart phones, mp3 players, digital frames, thumb drives and gaming stations will continue to provide opportunities for criminals and malware to infiltrate a company’s security borders due to their capabilities for storage, computing and Wi-Fi. Public access points such as those in coffee shops, bookstores, hotel lobbies, and airports will continue to be distribution points for malware or attack vectors used by malicious entities.
4. Communication services such as email, instant messaging, as well as file sharing will continue to be abused by content threats such as image spam, malicious URLs and attachments via targeted and localized social engineered themes.
5. Data protection and software security strategies will become standard in the commercial software lifecycle. This will also put a focus on data encryption technologies during storage and transit particularly in the vetting of data access in the information and distribution chain.
--Abhiz
The report talks about the growth of web threats, which increased yearly up to 2006 but seems to have slowed down over the last twelve months. They also notice a significant increase in the number of attacks on smart phones and other mobile gadgets. Take it with a grain of salt.
However, the most interesting part of the report is the pricing chart for black hat services:
adware from 2 to 20 cents per installation depending on location
exploit kit rental around $1 per hour
access to installed information stealing trojans around $80 each
DDoS around $100 per day
individual banking credentials from $50
Other notable findings from the report:
- The Windows Animated Cursor exploit (EXPL_ANICMOO) encompassed over 50 percent of all exploit codes to hit the Internet computing population. 74 percent of its infections this year came from Asia. The same holds true for TROJ_ANICMOO.AX, a related threat which embedded the exploit. 64 percent of computers infected with this were from China.
- The top malware finding was WORM_SPYBOT.IS and WORM_GAOBOT.DF. Both created botnets and worms that infected USB-connected devices.
- Nearly 50 percent of all threat infections come from North America, but Asian countries are also experiencing a growth -- 40 percent of infections stem from that region.
-Social networking communities and user-created content such as blog sites became infection vectors due to attacks on their underlying Web 2.0 technologies, particularly cross-site scripting and streaming technologies.
- Infection volumes nearly quadrupled between September and November 2007, indicating that malware authors took advantage of the holiday seasons as an opportunity to send spam or deploy spyware while users are shopping online.
- In 2007, the top online commerce site attacked by phishers was still global auction site eBay and sister company PayPal. Financial institutions, especially those based in North America, also experienced a high volume of phising attacks.
2008 Forecast
Based on the emerging trends of this year, the following are Trend Micro’s forecasts for the 2008 threat landscape:
1. Legacy code used in operating systems and vulnerabilities in popular applications will continue to be attacked in the effort to inject in-process malicious code that criminals can exploit to run malware as they attempt to steal confidential and proprietary information.
2. High-profile Web sites that run the gamut of social networking, banking/financial, online gaming, search engine, travel, commercial ticketing, local government sectors, news, job, blogging, and e-commerce sites for auction and shopping will continue to be the most sought-after attack vectors by criminals to host links to phishing and identity theft code.
3. Unmanaged devices such as smart phones, mp3 players, digital frames, thumb drives and gaming stations will continue to provide opportunities for criminals and malware to infiltrate a company’s security borders due to their capabilities for storage, computing and Wi-Fi. Public access points such as those in coffee shops, bookstores, hotel lobbies, and airports will continue to be distribution points for malware or attack vectors used by malicious entities.
4. Communication services such as email, instant messaging, as well as file sharing will continue to be abused by content threats such as image spam, malicious URLs and attachments via targeted and localized social engineered themes.
5. Data protection and software security strategies will become standard in the commercial software lifecycle. This will also put a focus on data encryption technologies during storage and transit particularly in the vetting of data access in the information and distribution chain.
--Abhiz
TrendMicro releases Blackhat pricing
Trend Micro has released its 2007 Annual Roundup and 2008 Forecast. The report contains a few interesting points that could be new compared to other reports.
The report talks about the growth of web threats, which increased yearly up to 2006 but seems to have slowed down over the last twelve months. They also notice a significant increase in the number of attacks on smart phones and other mobile gadgets. Take it with a grain of salt.
However, the most interesting part of the report is the pricing chart for black hat services:
adware from 2 to 20 cents per installation depending on location
exploit kit rental around $1 per hour
access to installed information stealing trojans around $80 each
DDoS around $100 per day
individual banking credentials from $50
Other notable findings from the report:
- The Windows Animated Cursor exploit (EXPL_ANICMOO) encompassed over 50 percent of all exploit codes to hit the Internet computing population. 74 percent of its infections this year came from Asia. The same holds true for TROJ_ANICMOO.AX, a related threat which embedded the exploit. 64 percent of computers infected with this were from China.
- The top malware finding was WORM_SPYBOT.IS and WORM_GAOBOT.DF. Both created botnets and worms that infected USB-connected devices.
- Nearly 50 percent of all threat infections come from North America, but Asian countries are also experiencing a growth -- 40 percent of infections stem from that region.
-Social networking communities and user-created content such as blog sites became infection vectors due to attacks on their underlying Web 2.0 technologies, particularly cross-site scripting and streaming technologies.
- Infection volumes nearly quadrupled between September and November 2007, indicating that malware authors took advantage of the holiday seasons as an opportunity to send spam or deploy spyware while users are shopping online.
- In 2007, the top online commerce site attacked by phishers was still global auction site eBay and sister company PayPal. Financial institutions, especially those based in North America, also experienced a high volume of phising attacks.
2008 Forecast
Based on the emerging trends of this year, the following are Trend Micro’s forecasts for the 2008 threat landscape:
1. Legacy code used in operating systems and vulnerabilities in popular applications will continue to be attacked in the effort to inject in-process malicious code that criminals can exploit to run malware as they attempt to steal confidential and proprietary information.
2. High-profile Web sites that run the gamut of social networking, banking/financial, online gaming, search engine, travel, commercial ticketing, local government sectors, news, job, blogging, and e-commerce sites for auction and shopping will continue to be the most sought-after attack vectors by criminals to host links to phishing and identity theft code.
3. Unmanaged devices such as smart phones, mp3 players, digital frames, thumb drives and gaming stations will continue to provide opportunities for criminals and malware to infiltrate a company’s security borders due to their capabilities for storage, computing and Wi-Fi. Public access points such as those in coffee shops, bookstores, hotel lobbies, and airports will continue to be distribution points for malware or attack vectors used by malicious entities.
4. Communication services such as email, instant messaging, as well as file sharing will continue to be abused by content threats such as image spam, malicious URLs and attachments via targeted and localized social engineered themes.
5. Data protection and software security strategies will become standard in the commercial software lifecycle. This will also put a focus on data encryption technologies during storage and transit particularly in the vetting of data access in the information and distribution chain.
--Abhiz
The report talks about the growth of web threats, which increased yearly up to 2006 but seems to have slowed down over the last twelve months. They also notice a significant increase in the number of attacks on smart phones and other mobile gadgets. Take it with a grain of salt.
However, the most interesting part of the report is the pricing chart for black hat services:
adware from 2 to 20 cents per installation depending on location
exploit kit rental around $1 per hour
access to installed information stealing trojans around $80 each
DDoS around $100 per day
individual banking credentials from $50
Other notable findings from the report:
- The Windows Animated Cursor exploit (EXPL_ANICMOO) encompassed over 50 percent of all exploit codes to hit the Internet computing population. 74 percent of its infections this year came from Asia. The same holds true for TROJ_ANICMOO.AX, a related threat which embedded the exploit. 64 percent of computers infected with this were from China.
- The top malware finding was WORM_SPYBOT.IS and WORM_GAOBOT.DF. Both created botnets and worms that infected USB-connected devices.
- Nearly 50 percent of all threat infections come from North America, but Asian countries are also experiencing a growth -- 40 percent of infections stem from that region.
-Social networking communities and user-created content such as blog sites became infection vectors due to attacks on their underlying Web 2.0 technologies, particularly cross-site scripting and streaming technologies.
- Infection volumes nearly quadrupled between September and November 2007, indicating that malware authors took advantage of the holiday seasons as an opportunity to send spam or deploy spyware while users are shopping online.
- In 2007, the top online commerce site attacked by phishers was still global auction site eBay and sister company PayPal. Financial institutions, especially those based in North America, also experienced a high volume of phising attacks.
2008 Forecast
Based on the emerging trends of this year, the following are Trend Micro’s forecasts for the 2008 threat landscape:
1. Legacy code used in operating systems and vulnerabilities in popular applications will continue to be attacked in the effort to inject in-process malicious code that criminals can exploit to run malware as they attempt to steal confidential and proprietary information.
2. High-profile Web sites that run the gamut of social networking, banking/financial, online gaming, search engine, travel, commercial ticketing, local government sectors, news, job, blogging, and e-commerce sites for auction and shopping will continue to be the most sought-after attack vectors by criminals to host links to phishing and identity theft code.
3. Unmanaged devices such as smart phones, mp3 players, digital frames, thumb drives and gaming stations will continue to provide opportunities for criminals and malware to infiltrate a company’s security borders due to their capabilities for storage, computing and Wi-Fi. Public access points such as those in coffee shops, bookstores, hotel lobbies, and airports will continue to be distribution points for malware or attack vectors used by malicious entities.
4. Communication services such as email, instant messaging, as well as file sharing will continue to be abused by content threats such as image spam, malicious URLs and attachments via targeted and localized social engineered themes.
5. Data protection and software security strategies will become standard in the commercial software lifecycle. This will also put a focus on data encryption technologies during storage and transit particularly in the vetting of data access in the information and distribution chain.
--Abhiz
TrendMicro releases Blackhat pricing
Trend Micro has released its 2007 Annual Roundup and 2008 Forecast. The report contains a few interesting points that could be new compared to other reports.
The report talks about the growth of web threats, which increased yearly up to 2006 but seems to have slowed down over the last twelve months. They also notice a significant increase in the number of attacks on smart phones and other mobile gadgets. Take it with a grain of salt.
However, the most interesting part of the report is the pricing chart for black hat services:
adware from 2 to 20 cents per installation depending on location
exploit kit rental around $1 per hour
access to installed information stealing trojans around $80 each
DDoS around $100 per day
individual banking credentials from $50
Other notable findings from the report:
- The Windows Animated Cursor exploit (EXPL_ANICMOO) encompassed over 50 percent of all exploit codes to hit the Internet computing population. 74 percent of its infections this year came from Asia. The same holds true for TROJ_ANICMOO.AX, a related threat which embedded the exploit. 64 percent of computers infected with this were from China.
- The top malware finding was WORM_SPYBOT.IS and WORM_GAOBOT.DF. Both created botnets and worms that infected USB-connected devices.
- Nearly 50 percent of all threat infections come from North America, but Asian countries are also experiencing a growth -- 40 percent of infections stem from that region.
-Social networking communities and user-created content such as blog sites became infection vectors due to attacks on their underlying Web 2.0 technologies, particularly cross-site scripting and streaming technologies.
- Infection volumes nearly quadrupled between September and November 2007, indicating that malware authors took advantage of the holiday seasons as an opportunity to send spam or deploy spyware while users are shopping online.
- In 2007, the top online commerce site attacked by phishers was still global auction site eBay and sister company PayPal. Financial institutions, especially those based in North America, also experienced a high volume of phising attacks.
2008 Forecast
Based on the emerging trends of this year, the following are Trend Micro’s forecasts for the 2008 threat landscape:
1. Legacy code used in operating systems and vulnerabilities in popular applications will continue to be attacked in the effort to inject in-process malicious code that criminals can exploit to run malware as they attempt to steal confidential and proprietary information.
2. High-profile Web sites that run the gamut of social networking, banking/financial, online gaming, search engine, travel, commercial ticketing, local government sectors, news, job, blogging, and e-commerce sites for auction and shopping will continue to be the most sought-after attack vectors by criminals to host links to phishing and identity theft code.
3. Unmanaged devices such as smart phones, mp3 players, digital frames, thumb drives and gaming stations will continue to provide opportunities for criminals and malware to infiltrate a company’s security borders due to their capabilities for storage, computing and Wi-Fi. Public access points such as those in coffee shops, bookstores, hotel lobbies, and airports will continue to be distribution points for malware or attack vectors used by malicious entities.
4. Communication services such as email, instant messaging, as well as file sharing will continue to be abused by content threats such as image spam, malicious URLs and attachments via targeted and localized social engineered themes.
5. Data protection and software security strategies will become standard in the commercial software lifecycle. This will also put a focus on data encryption technologies during storage and transit particularly in the vetting of data access in the information and distribution chain.
--Abhiz
The report talks about the growth of web threats, which increased yearly up to 2006 but seems to have slowed down over the last twelve months. They also notice a significant increase in the number of attacks on smart phones and other mobile gadgets. Take it with a grain of salt.
However, the most interesting part of the report is the pricing chart for black hat services:
adware from 2 to 20 cents per installation depending on location
exploit kit rental around $1 per hour
access to installed information stealing trojans around $80 each
DDoS around $100 per day
individual banking credentials from $50
Other notable findings from the report:
- The Windows Animated Cursor exploit (EXPL_ANICMOO) encompassed over 50 percent of all exploit codes to hit the Internet computing population. 74 percent of its infections this year came from Asia. The same holds true for TROJ_ANICMOO.AX, a related threat which embedded the exploit. 64 percent of computers infected with this were from China.
- The top malware finding was WORM_SPYBOT.IS and WORM_GAOBOT.DF. Both created botnets and worms that infected USB-connected devices.
- Nearly 50 percent of all threat infections come from North America, but Asian countries are also experiencing a growth -- 40 percent of infections stem from that region.
-Social networking communities and user-created content such as blog sites became infection vectors due to attacks on their underlying Web 2.0 technologies, particularly cross-site scripting and streaming technologies.
- Infection volumes nearly quadrupled between September and November 2007, indicating that malware authors took advantage of the holiday seasons as an opportunity to send spam or deploy spyware while users are shopping online.
- In 2007, the top online commerce site attacked by phishers was still global auction site eBay and sister company PayPal. Financial institutions, especially those based in North America, also experienced a high volume of phising attacks.
2008 Forecast
Based on the emerging trends of this year, the following are Trend Micro’s forecasts for the 2008 threat landscape:
1. Legacy code used in operating systems and vulnerabilities in popular applications will continue to be attacked in the effort to inject in-process malicious code that criminals can exploit to run malware as they attempt to steal confidential and proprietary information.
2. High-profile Web sites that run the gamut of social networking, banking/financial, online gaming, search engine, travel, commercial ticketing, local government sectors, news, job, blogging, and e-commerce sites for auction and shopping will continue to be the most sought-after attack vectors by criminals to host links to phishing and identity theft code.
3. Unmanaged devices such as smart phones, mp3 players, digital frames, thumb drives and gaming stations will continue to provide opportunities for criminals and malware to infiltrate a company’s security borders due to their capabilities for storage, computing and Wi-Fi. Public access points such as those in coffee shops, bookstores, hotel lobbies, and airports will continue to be distribution points for malware or attack vectors used by malicious entities.
4. Communication services such as email, instant messaging, as well as file sharing will continue to be abused by content threats such as image spam, malicious URLs and attachments via targeted and localized social engineered themes.
5. Data protection and software security strategies will become standard in the commercial software lifecycle. This will also put a focus on data encryption technologies during storage and transit particularly in the vetting of data access in the information and distribution chain.
--Abhiz
TrendMicro releases Blackhat pricing
Trend Micro has released its 2007 Annual Roundup and 2008 Forecast. The report contains a few interesting points that could be new compared to other reports.
The report talks about the growth of web threats, which increased yearly up to 2006 but seems to have slowed down over the last twelve months. They also notice a significant increase in the number of attacks on smart phones and other mobile gadgets. Take it with a grain of salt.
However, the most interesting part of the report is the pricing chart for black hat services:
adware from 2 to 20 cents per installation depending on location
exploit kit rental around $1 per hour
access to installed information stealing trojans around $80 each
DDoS around $100 per day
individual banking credentials from $50
Other notable findings from the report:
- The Windows Animated Cursor exploit (EXPL_ANICMOO) encompassed over 50 percent of all exploit codes to hit the Internet computing population. 74 percent of its infections this year came from Asia. The same holds true for TROJ_ANICMOO.AX, a related threat which embedded the exploit. 64 percent of computers infected with this were from China.
- The top malware finding was WORM_SPYBOT.IS and WORM_GAOBOT.DF. Both created botnets and worms that infected USB-connected devices.
- Nearly 50 percent of all threat infections come from North America, but Asian countries are also experiencing a growth -- 40 percent of infections stem from that region.
-Social networking communities and user-created content such as blog sites became infection vectors due to attacks on their underlying Web 2.0 technologies, particularly cross-site scripting and streaming technologies.
- Infection volumes nearly quadrupled between September and November 2007, indicating that malware authors took advantage of the holiday seasons as an opportunity to send spam or deploy spyware while users are shopping online.
- In 2007, the top online commerce site attacked by phishers was still global auction site eBay and sister company PayPal. Financial institutions, especially those based in North America, also experienced a high volume of phising attacks.
2008 Forecast
Based on the emerging trends of this year, the following are Trend Micro’s forecasts for the 2008 threat landscape:
1. Legacy code used in operating systems and vulnerabilities in popular applications will continue to be attacked in the effort to inject in-process malicious code that criminals can exploit to run malware as they attempt to steal confidential and proprietary information.
2. High-profile Web sites that run the gamut of social networking, banking/financial, online gaming, search engine, travel, commercial ticketing, local government sectors, news, job, blogging, and e-commerce sites for auction and shopping will continue to be the most sought-after attack vectors by criminals to host links to phishing and identity theft code.
3. Unmanaged devices such as smart phones, mp3 players, digital frames, thumb drives and gaming stations will continue to provide opportunities for criminals and malware to infiltrate a company’s security borders due to their capabilities for storage, computing and Wi-Fi. Public access points such as those in coffee shops, bookstores, hotel lobbies, and airports will continue to be distribution points for malware or attack vectors used by malicious entities.
4. Communication services such as email, instant messaging, as well as file sharing will continue to be abused by content threats such as image spam, malicious URLs and attachments via targeted and localized social engineered themes.
5. Data protection and software security strategies will become standard in the commercial software lifecycle. This will also put a focus on data encryption technologies during storage and transit particularly in the vetting of data access in the information and distribution chain.
--Abhiz
The report talks about the growth of web threats, which increased yearly up to 2006 but seems to have slowed down over the last twelve months. They also notice a significant increase in the number of attacks on smart phones and other mobile gadgets. Take it with a grain of salt.
However, the most interesting part of the report is the pricing chart for black hat services:
adware from 2 to 20 cents per installation depending on location
exploit kit rental around $1 per hour
access to installed information stealing trojans around $80 each
DDoS around $100 per day
individual banking credentials from $50
Other notable findings from the report:
- The Windows Animated Cursor exploit (EXPL_ANICMOO) encompassed over 50 percent of all exploit codes to hit the Internet computing population. 74 percent of its infections this year came from Asia. The same holds true for TROJ_ANICMOO.AX, a related threat which embedded the exploit. 64 percent of computers infected with this were from China.
- The top malware finding was WORM_SPYBOT.IS and WORM_GAOBOT.DF. Both created botnets and worms that infected USB-connected devices.
- Nearly 50 percent of all threat infections come from North America, but Asian countries are also experiencing a growth -- 40 percent of infections stem from that region.
-Social networking communities and user-created content such as blog sites became infection vectors due to attacks on their underlying Web 2.0 technologies, particularly cross-site scripting and streaming technologies.
- Infection volumes nearly quadrupled between September and November 2007, indicating that malware authors took advantage of the holiday seasons as an opportunity to send spam or deploy spyware while users are shopping online.
- In 2007, the top online commerce site attacked by phishers was still global auction site eBay and sister company PayPal. Financial institutions, especially those based in North America, also experienced a high volume of phising attacks.
2008 Forecast
Based on the emerging trends of this year, the following are Trend Micro’s forecasts for the 2008 threat landscape:
1. Legacy code used in operating systems and vulnerabilities in popular applications will continue to be attacked in the effort to inject in-process malicious code that criminals can exploit to run malware as they attempt to steal confidential and proprietary information.
2. High-profile Web sites that run the gamut of social networking, banking/financial, online gaming, search engine, travel, commercial ticketing, local government sectors, news, job, blogging, and e-commerce sites for auction and shopping will continue to be the most sought-after attack vectors by criminals to host links to phishing and identity theft code.
3. Unmanaged devices such as smart phones, mp3 players, digital frames, thumb drives and gaming stations will continue to provide opportunities for criminals and malware to infiltrate a company’s security borders due to their capabilities for storage, computing and Wi-Fi. Public access points such as those in coffee shops, bookstores, hotel lobbies, and airports will continue to be distribution points for malware or attack vectors used by malicious entities.
4. Communication services such as email, instant messaging, as well as file sharing will continue to be abused by content threats such as image spam, malicious URLs and attachments via targeted and localized social engineered themes.
5. Data protection and software security strategies will become standard in the commercial software lifecycle. This will also put a focus on data encryption technologies during storage and transit particularly in the vetting of data access in the information and distribution chain.
--Abhiz
TrendMicro releases Blackhat pricing
Trend Micro has released its 2007 Annual Roundup and 2008 Forecast. The report contains a few interesting points that could be new compared to other reports.
The report talks about the growth of web threats, which increased yearly up to 2006 but seems to have slowed down over the last twelve months. They also notice a significant increase in the number of attacks on smart phones and other mobile gadgets. Take it with a grain of salt.
However, the most interesting part of the report is the pricing chart for black hat services:
adware from 2 to 20 cents per installation depending on location
exploit kit rental around $1 per hour
access to installed information stealing trojans around $80 each
DDoS around $100 per day
individual banking credentials from $50
Other notable findings from the report:
- The Windows Animated Cursor exploit (EXPL_ANICMOO) encompassed over 50 percent of all exploit codes to hit the Internet computing population. 74 percent of its infections this year came from Asia. The same holds true for TROJ_ANICMOO.AX, a related threat which embedded the exploit. 64 percent of computers infected with this were from China.
- The top malware finding was WORM_SPYBOT.IS and WORM_GAOBOT.DF. Both created botnets and worms that infected USB-connected devices.
- Nearly 50 percent of all threat infections come from North America, but Asian countries are also experiencing a growth -- 40 percent of infections stem from that region.
-Social networking communities and user-created content such as blog sites became infection vectors due to attacks on their underlying Web 2.0 technologies, particularly cross-site scripting and streaming technologies.
- Infection volumes nearly quadrupled between September and November 2007, indicating that malware authors took advantage of the holiday seasons as an opportunity to send spam or deploy spyware while users are shopping online.
- In 2007, the top online commerce site attacked by phishers was still global auction site eBay and sister company PayPal. Financial institutions, especially those based in North America, also experienced a high volume of phising attacks.
2008 Forecast
Based on the emerging trends of this year, the following are Trend Micro’s forecasts for the 2008 threat landscape:
1. Legacy code used in operating systems and vulnerabilities in popular applications will continue to be attacked in the effort to inject in-process malicious code that criminals can exploit to run malware as they attempt to steal confidential and proprietary information.
2. High-profile Web sites that run the gamut of social networking, banking/financial, online gaming, search engine, travel, commercial ticketing, local government sectors, news, job, blogging, and e-commerce sites for auction and shopping will continue to be the most sought-after attack vectors by criminals to host links to phishing and identity theft code.
3. Unmanaged devices such as smart phones, mp3 players, digital frames, thumb drives and gaming stations will continue to provide opportunities for criminals and malware to infiltrate a company’s security borders due to their capabilities for storage, computing and Wi-Fi. Public access points such as those in coffee shops, bookstores, hotel lobbies, and airports will continue to be distribution points for malware or attack vectors used by malicious entities.
4. Communication services such as email, instant messaging, as well as file sharing will continue to be abused by content threats such as image spam, malicious URLs and attachments via targeted and localized social engineered themes.
5. Data protection and software security strategies will become standard in the commercial software lifecycle. This will also put a focus on data encryption technologies during storage and transit particularly in the vetting of data access in the information and distribution chain.
--Abhiz
The report talks about the growth of web threats, which increased yearly up to 2006 but seems to have slowed down over the last twelve months. They also notice a significant increase in the number of attacks on smart phones and other mobile gadgets. Take it with a grain of salt.
However, the most interesting part of the report is the pricing chart for black hat services:
adware from 2 to 20 cents per installation depending on location
exploit kit rental around $1 per hour
access to installed information stealing trojans around $80 each
DDoS around $100 per day
individual banking credentials from $50
Other notable findings from the report:
- The Windows Animated Cursor exploit (EXPL_ANICMOO) encompassed over 50 percent of all exploit codes to hit the Internet computing population. 74 percent of its infections this year came from Asia. The same holds true for TROJ_ANICMOO.AX, a related threat which embedded the exploit. 64 percent of computers infected with this were from China.
- The top malware finding was WORM_SPYBOT.IS and WORM_GAOBOT.DF. Both created botnets and worms that infected USB-connected devices.
- Nearly 50 percent of all threat infections come from North America, but Asian countries are also experiencing a growth -- 40 percent of infections stem from that region.
-Social networking communities and user-created content such as blog sites became infection vectors due to attacks on their underlying Web 2.0 technologies, particularly cross-site scripting and streaming technologies.
- Infection volumes nearly quadrupled between September and November 2007, indicating that malware authors took advantage of the holiday seasons as an opportunity to send spam or deploy spyware while users are shopping online.
- In 2007, the top online commerce site attacked by phishers was still global auction site eBay and sister company PayPal. Financial institutions, especially those based in North America, also experienced a high volume of phising attacks.
2008 Forecast
Based on the emerging trends of this year, the following are Trend Micro’s forecasts for the 2008 threat landscape:
1. Legacy code used in operating systems and vulnerabilities in popular applications will continue to be attacked in the effort to inject in-process malicious code that criminals can exploit to run malware as they attempt to steal confidential and proprietary information.
2. High-profile Web sites that run the gamut of social networking, banking/financial, online gaming, search engine, travel, commercial ticketing, local government sectors, news, job, blogging, and e-commerce sites for auction and shopping will continue to be the most sought-after attack vectors by criminals to host links to phishing and identity theft code.
3. Unmanaged devices such as smart phones, mp3 players, digital frames, thumb drives and gaming stations will continue to provide opportunities for criminals and malware to infiltrate a company’s security borders due to their capabilities for storage, computing and Wi-Fi. Public access points such as those in coffee shops, bookstores, hotel lobbies, and airports will continue to be distribution points for malware or attack vectors used by malicious entities.
4. Communication services such as email, instant messaging, as well as file sharing will continue to be abused by content threats such as image spam, malicious URLs and attachments via targeted and localized social engineered themes.
5. Data protection and software security strategies will become standard in the commercial software lifecycle. This will also put a focus on data encryption technologies during storage and transit particularly in the vetting of data access in the information and distribution chain.
--Abhiz
TrendMicro releases Blackhat pricing
Trend Micro has released its 2007 Annual Roundup and 2008 Forecast. The report contains a few interesting points that could be new compared to other reports.
The report talks about the growth of web threats, which increased yearly up to 2006 but seems to have slowed down over the last twelve months. They also notice a significant increase in the number of attacks on smart phones and other mobile gadgets. Take it with a grain of salt.
However, the most interesting part of the report is the pricing chart for black hat services:
adware from 2 to 20 cents per installation depending on location
exploit kit rental around $1 per hour
access to installed information stealing trojans around $80 each
DDoS around $100 per day
individual banking credentials from $50
Other notable findings from the report:
- The Windows Animated Cursor exploit (EXPL_ANICMOO) encompassed over 50 percent of all exploit codes to hit the Internet computing population. 74 percent of its infections this year came from Asia. The same holds true for TROJ_ANICMOO.AX, a related threat which embedded the exploit. 64 percent of computers infected with this were from China.
- The top malware finding was WORM_SPYBOT.IS and WORM_GAOBOT.DF. Both created botnets and worms that infected USB-connected devices.
- Nearly 50 percent of all threat infections come from North America, but Asian countries are also experiencing a growth -- 40 percent of infections stem from that region.
-Social networking communities and user-created content such as blog sites became infection vectors due to attacks on their underlying Web 2.0 technologies, particularly cross-site scripting and streaming technologies.
- Infection volumes nearly quadrupled between September and November 2007, indicating that malware authors took advantage of the holiday seasons as an opportunity to send spam or deploy spyware while users are shopping online.
- In 2007, the top online commerce site attacked by phishers was still global auction site eBay and sister company PayPal. Financial institutions, especially those based in North America, also experienced a high volume of phising attacks.
2008 Forecast
Based on the emerging trends of this year, the following are Trend Micro’s forecasts for the 2008 threat landscape:
1. Legacy code used in operating systems and vulnerabilities in popular applications will continue to be attacked in the effort to inject in-process malicious code that criminals can exploit to run malware as they attempt to steal confidential and proprietary information.
2. High-profile Web sites that run the gamut of social networking, banking/financial, online gaming, search engine, travel, commercial ticketing, local government sectors, news, job, blogging, and e-commerce sites for auction and shopping will continue to be the most sought-after attack vectors by criminals to host links to phishing and identity theft code.
3. Unmanaged devices such as smart phones, mp3 players, digital frames, thumb drives and gaming stations will continue to provide opportunities for criminals and malware to infiltrate a company’s security borders due to their capabilities for storage, computing and Wi-Fi. Public access points such as those in coffee shops, bookstores, hotel lobbies, and airports will continue to be distribution points for malware or attack vectors used by malicious entities.
4. Communication services such as email, instant messaging, as well as file sharing will continue to be abused by content threats such as image spam, malicious URLs and attachments via targeted and localized social engineered themes.
5. Data protection and software security strategies will become standard in the commercial software lifecycle. This will also put a focus on data encryption technologies during storage and transit particularly in the vetting of data access in the information and distribution chain.
--Abhiz
The report talks about the growth of web threats, which increased yearly up to 2006 but seems to have slowed down over the last twelve months. They also notice a significant increase in the number of attacks on smart phones and other mobile gadgets. Take it with a grain of salt.
However, the most interesting part of the report is the pricing chart for black hat services:
adware from 2 to 20 cents per installation depending on location
exploit kit rental around $1 per hour
access to installed information stealing trojans around $80 each
DDoS around $100 per day
individual banking credentials from $50
Other notable findings from the report:
- The Windows Animated Cursor exploit (EXPL_ANICMOO) encompassed over 50 percent of all exploit codes to hit the Internet computing population. 74 percent of its infections this year came from Asia. The same holds true for TROJ_ANICMOO.AX, a related threat which embedded the exploit. 64 percent of computers infected with this were from China.
- The top malware finding was WORM_SPYBOT.IS and WORM_GAOBOT.DF. Both created botnets and worms that infected USB-connected devices.
- Nearly 50 percent of all threat infections come from North America, but Asian countries are also experiencing a growth -- 40 percent of infections stem from that region.
-Social networking communities and user-created content such as blog sites became infection vectors due to attacks on their underlying Web 2.0 technologies, particularly cross-site scripting and streaming technologies.
- Infection volumes nearly quadrupled between September and November 2007, indicating that malware authors took advantage of the holiday seasons as an opportunity to send spam or deploy spyware while users are shopping online.
- In 2007, the top online commerce site attacked by phishers was still global auction site eBay and sister company PayPal. Financial institutions, especially those based in North America, also experienced a high volume of phising attacks.
2008 Forecast
Based on the emerging trends of this year, the following are Trend Micro’s forecasts for the 2008 threat landscape:
1. Legacy code used in operating systems and vulnerabilities in popular applications will continue to be attacked in the effort to inject in-process malicious code that criminals can exploit to run malware as they attempt to steal confidential and proprietary information.
2. High-profile Web sites that run the gamut of social networking, banking/financial, online gaming, search engine, travel, commercial ticketing, local government sectors, news, job, blogging, and e-commerce sites for auction and shopping will continue to be the most sought-after attack vectors by criminals to host links to phishing and identity theft code.
3. Unmanaged devices such as smart phones, mp3 players, digital frames, thumb drives and gaming stations will continue to provide opportunities for criminals and malware to infiltrate a company’s security borders due to their capabilities for storage, computing and Wi-Fi. Public access points such as those in coffee shops, bookstores, hotel lobbies, and airports will continue to be distribution points for malware or attack vectors used by malicious entities.
4. Communication services such as email, instant messaging, as well as file sharing will continue to be abused by content threats such as image spam, malicious URLs and attachments via targeted and localized social engineered themes.
5. Data protection and software security strategies will become standard in the commercial software lifecycle. This will also put a focus on data encryption technologies during storage and transit particularly in the vetting of data access in the information and distribution chain.
--Abhiz
TrendMicro releases Blackhat pricing
Trend Micro has released its 2007 Annual Roundup and 2008 Forecast. The report contains a few interesting points that could be new compared to other reports.
The report talks about the growth of web threats, which increased yearly up to 2006 but seems to have slowed down over the last twelve months. They also notice a significant increase in the number of attacks on smart phones and other mobile gadgets. Take it with a grain of salt.
However, the most interesting part of the report is the pricing chart for black hat services:
adware from 2 to 20 cents per installation depending on location
exploit kit rental around $1 per hour
access to installed information stealing trojans around $80 each
DDoS around $100 per day
individual banking credentials from $50
Other notable findings from the report:
- The Windows Animated Cursor exploit (EXPL_ANICMOO) encompassed over 50 percent of all exploit codes to hit the Internet computing population. 74 percent of its infections this year came from Asia. The same holds true for TROJ_ANICMOO.AX, a related threat which embedded the exploit. 64 percent of computers infected with this were from China.
- The top malware finding was WORM_SPYBOT.IS and WORM_GAOBOT.DF. Both created botnets and worms that infected USB-connected devices.
- Nearly 50 percent of all threat infections come from North America, but Asian countries are also experiencing a growth -- 40 percent of infections stem from that region.
-Social networking communities and user-created content such as blog sites became infection vectors due to attacks on their underlying Web 2.0 technologies, particularly cross-site scripting and streaming technologies.
- Infection volumes nearly quadrupled between September and November 2007, indicating that malware authors took advantage of the holiday seasons as an opportunity to send spam or deploy spyware while users are shopping online.
- In 2007, the top online commerce site attacked by phishers was still global auction site eBay and sister company PayPal. Financial institutions, especially those based in North America, also experienced a high volume of phising attacks.
2008 Forecast
Based on the emerging trends of this year, the following are Trend Micro’s forecasts for the 2008 threat landscape:
1. Legacy code used in operating systems and vulnerabilities in popular applications will continue to be attacked in the effort to inject in-process malicious code that criminals can exploit to run malware as they attempt to steal confidential and proprietary information.
2. High-profile Web sites that run the gamut of social networking, banking/financial, online gaming, search engine, travel, commercial ticketing, local government sectors, news, job, blogging, and e-commerce sites for auction and shopping will continue to be the most sought-after attack vectors by criminals to host links to phishing and identity theft code.
3. Unmanaged devices such as smart phones, mp3 players, digital frames, thumb drives and gaming stations will continue to provide opportunities for criminals and malware to infiltrate a company’s security borders due to their capabilities for storage, computing and Wi-Fi. Public access points such as those in coffee shops, bookstores, hotel lobbies, and airports will continue to be distribution points for malware or attack vectors used by malicious entities.
4. Communication services such as email, instant messaging, as well as file sharing will continue to be abused by content threats such as image spam, malicious URLs and attachments via targeted and localized social engineered themes.
5. Data protection and software security strategies will become standard in the commercial software lifecycle. This will also put a focus on data encryption technologies during storage and transit particularly in the vetting of data access in the information and distribution chain.
--Abhiz
The report talks about the growth of web threats, which increased yearly up to 2006 but seems to have slowed down over the last twelve months. They also notice a significant increase in the number of attacks on smart phones and other mobile gadgets. Take it with a grain of salt.
However, the most interesting part of the report is the pricing chart for black hat services:
adware from 2 to 20 cents per installation depending on location
exploit kit rental around $1 per hour
access to installed information stealing trojans around $80 each
DDoS around $100 per day
individual banking credentials from $50
Other notable findings from the report:
- The Windows Animated Cursor exploit (EXPL_ANICMOO) encompassed over 50 percent of all exploit codes to hit the Internet computing population. 74 percent of its infections this year came from Asia. The same holds true for TROJ_ANICMOO.AX, a related threat which embedded the exploit. 64 percent of computers infected with this were from China.
- The top malware finding was WORM_SPYBOT.IS and WORM_GAOBOT.DF. Both created botnets and worms that infected USB-connected devices.
- Nearly 50 percent of all threat infections come from North America, but Asian countries are also experiencing a growth -- 40 percent of infections stem from that region.
-Social networking communities and user-created content such as blog sites became infection vectors due to attacks on their underlying Web 2.0 technologies, particularly cross-site scripting and streaming technologies.
- Infection volumes nearly quadrupled between September and November 2007, indicating that malware authors took advantage of the holiday seasons as an opportunity to send spam or deploy spyware while users are shopping online.
- In 2007, the top online commerce site attacked by phishers was still global auction site eBay and sister company PayPal. Financial institutions, especially those based in North America, also experienced a high volume of phising attacks.
2008 Forecast
Based on the emerging trends of this year, the following are Trend Micro’s forecasts for the 2008 threat landscape:
1. Legacy code used in operating systems and vulnerabilities in popular applications will continue to be attacked in the effort to inject in-process malicious code that criminals can exploit to run malware as they attempt to steal confidential and proprietary information.
2. High-profile Web sites that run the gamut of social networking, banking/financial, online gaming, search engine, travel, commercial ticketing, local government sectors, news, job, blogging, and e-commerce sites for auction and shopping will continue to be the most sought-after attack vectors by criminals to host links to phishing and identity theft code.
3. Unmanaged devices such as smart phones, mp3 players, digital frames, thumb drives and gaming stations will continue to provide opportunities for criminals and malware to infiltrate a company’s security borders due to their capabilities for storage, computing and Wi-Fi. Public access points such as those in coffee shops, bookstores, hotel lobbies, and airports will continue to be distribution points for malware or attack vectors used by malicious entities.
4. Communication services such as email, instant messaging, as well as file sharing will continue to be abused by content threats such as image spam, malicious URLs and attachments via targeted and localized social engineered themes.
5. Data protection and software security strategies will become standard in the commercial software lifecycle. This will also put a focus on data encryption technologies during storage and transit particularly in the vetting of data access in the information and distribution chain.
--Abhiz
Wanna root FTP servers ?
meoryprof.info is offering a crimeware package that can infect more than 9000 corporations, its a kind of software as a service model that they are using, they have already compromised the hosts and now selling it as a crimeware to make profits.
The idea is simple you select a website and you can do multiple things like upload keyloggers, bots and do iFrame injection, the best of all is these people have tried their best to make their malware undetectable.
Now this is called Organized Crime :)
meoryprof.info seems to be offline now
--Abhiz
The idea is simple you select a website and you can do multiple things like upload keyloggers, bots and do iFrame injection, the best of all is these people have tried their best to make their malware undetectable.
Now this is called Organized Crime :)
meoryprof.info seems to be offline now
--Abhiz
Wanna root FTP servers ?
meoryprof.info is offering a crimeware package that can infect more than 9000 corporations, its a kind of software as a service model that they are using, they have already compromised the hosts and now selling it as a crimeware to make profits.
The idea is simple you select a website and you can do multiple things like upload keyloggers, bots and do iFrame injection, the best of all is these people have tried their best to make their malware undetectable.
Now this is called Organized Crime :)
meoryprof.info seems to be offline now
--Abhiz
The idea is simple you select a website and you can do multiple things like upload keyloggers, bots and do iFrame injection, the best of all is these people have tried their best to make their malware undetectable.
Now this is called Organized Crime :)
meoryprof.info seems to be offline now
--Abhiz
Wanna root FTP servers ?
meoryprof.info is offering a crimeware package that can infect more than 9000 corporations, its a kind of software as a service model that they are using, they have already compromised the hosts and now selling it as a crimeware to make profits.
The idea is simple you select a website and you can do multiple things like upload keyloggers, bots and do iFrame injection, the best of all is these people have tried their best to make their malware undetectable.
Now this is called Organized Crime :)
meoryprof.info seems to be offline now
--Abhiz
The idea is simple you select a website and you can do multiple things like upload keyloggers, bots and do iFrame injection, the best of all is these people have tried their best to make their malware undetectable.
Now this is called Organized Crime :)
meoryprof.info seems to be offline now
--Abhiz
Wanna root FTP servers ?
meoryprof.info is offering a crimeware package that can infect more than 9000 corporations, its a kind of software as a service model that they are using, they have already compromised the hosts and now selling it as a crimeware to make profits.
The idea is simple you select a website and you can do multiple things like upload keyloggers, bots and do iFrame injection, the best of all is these people have tried their best to make their malware undetectable.
Now this is called Organized Crime :)
meoryprof.info seems to be offline now
--Abhiz
The idea is simple you select a website and you can do multiple things like upload keyloggers, bots and do iFrame injection, the best of all is these people have tried their best to make their malware undetectable.
Now this is called Organized Crime :)
meoryprof.info seems to be offline now
--Abhiz
Wanna root FTP servers ?
meoryprof.info is offering a crimeware package that can infect more than 9000 corporations, its a kind of software as a service model that they are using, they have already compromised the hosts and now selling it as a crimeware to make profits.
The idea is simple you select a website and you can do multiple things like upload keyloggers, bots and do iFrame injection, the best of all is these people have tried their best to make their malware undetectable.
Now this is called Organized Crime :)
meoryprof.info seems to be offline now
--Abhiz
The idea is simple you select a website and you can do multiple things like upload keyloggers, bots and do iFrame injection, the best of all is these people have tried their best to make their malware undetectable.
Now this is called Organized Crime :)
meoryprof.info seems to be offline now
--Abhiz
Wanna root FTP servers ?
meoryprof.info is offering a crimeware package that can infect more than 9000 corporations, its a kind of software as a service model that they are using, they have already compromised the hosts and now selling it as a crimeware to make profits.
The idea is simple you select a website and you can do multiple things like upload keyloggers, bots and do iFrame injection, the best of all is these people have tried their best to make their malware undetectable.
Now this is called Organized Crime :)
meoryprof.info seems to be offline now
--Abhiz
The idea is simple you select a website and you can do multiple things like upload keyloggers, bots and do iFrame injection, the best of all is these people have tried their best to make their malware undetectable.
Now this is called Organized Crime :)
meoryprof.info seems to be offline now
--Abhiz
Wanna root FTP servers ?
meoryprof.info is offering a crimeware package that can infect more than 9000 corporations, its a kind of software as a service model that they are using, they have already compromised the hosts and now selling it as a crimeware to make profits.
The idea is simple you select a website and you can do multiple things like upload keyloggers, bots and do iFrame injection, the best of all is these people have tried their best to make their malware undetectable.
Now this is called Organized Crime :)
meoryprof.info seems to be offline now
--Abhiz
The idea is simple you select a website and you can do multiple things like upload keyloggers, bots and do iFrame injection, the best of all is these people have tried their best to make their malware undetectable.
Now this is called Organized Crime :)
meoryprof.info seems to be offline now
--Abhiz
Wanna root FTP servers ?
meoryprof.info is offering a crimeware package that can infect more than 9000 corporations, its a kind of software as a service model that they are using, they have already compromised the hosts and now selling it as a crimeware to make profits.
The idea is simple you select a website and you can do multiple things like upload keyloggers, bots and do iFrame injection, the best of all is these people have tried their best to make their malware undetectable.
Now this is called Organized Crime :)
meoryprof.info seems to be offline now
--Abhiz
The idea is simple you select a website and you can do multiple things like upload keyloggers, bots and do iFrame injection, the best of all is these people have tried their best to make their malware undetectable.
Now this is called Organized Crime :)
meoryprof.info seems to be offline now
--Abhiz
Wanna root FTP servers ?
meoryprof.info is offering a crimeware package that can infect more than 9000 corporations, its a kind of software as a service model that they are using, they have already compromised the hosts and now selling it as a crimeware to make profits.
The idea is simple you select a website and you can do multiple things like upload keyloggers, bots and do iFrame injection, the best of all is these people have tried their best to make their malware undetectable.
Now this is called Organized Crime :)
meoryprof.info seems to be offline now
--Abhiz
The idea is simple you select a website and you can do multiple things like upload keyloggers, bots and do iFrame injection, the best of all is these people have tried their best to make their malware undetectable.
Now this is called Organized Crime :)
meoryprof.info seems to be offline now
--Abhiz
Wanna root FTP servers ?
meoryprof.info is offering a crimeware package that can infect more than 9000 corporations, its a kind of software as a service model that they are using, they have already compromised the hosts and now selling it as a crimeware to make profits.
The idea is simple you select a website and you can do multiple things like upload keyloggers, bots and do iFrame injection, the best of all is these people have tried their best to make their malware undetectable.
Now this is called Organized Crime :)
meoryprof.info seems to be offline now
--Abhiz
The idea is simple you select a website and you can do multiple things like upload keyloggers, bots and do iFrame injection, the best of all is these people have tried their best to make their malware undetectable.
Now this is called Organized Crime :)
meoryprof.info seems to be offline now
--Abhiz
Miss Identify - Detect hidden executable files on windows
Miss Identify is an excellent utilty which can be used to detect executable files on windows, regardless of their file extension, it is very similar to "file" tool in unix but it is has a special task, Detect only executables only. The tool looks very promising.
"Miss Identify is a program to find Win32 applications. In its default mode it displays the filename of any executable that does not have an executable extension (i.e. exe, dll, com, sys, cpl, hxs, hxi, olb, rll, or tlb). The program can also be run to display all executables encountered, regardless of the extension. This is handy when looking for all of the executables on a drive."
--Abhiz
"Miss Identify is a program to find Win32 applications. In its default mode it displays the filename of any executable that does not have an executable extension (i.e. exe, dll, com, sys, cpl, hxs, hxi, olb, rll, or tlb). The program can also be run to display all executables encountered, regardless of the extension. This is handy when looking for all of the executables on a drive."
--Abhiz
Miss Identify - Detect hidden executable files on windows
Miss Identify is an excellent utilty which can be used to detect executable files on windows, regardless of their file extension, it is very similar to "file" tool in unix but it is has a special task, Detect only executables only. The tool looks very promising.
"Miss Identify is a program to find Win32 applications. In its default mode it displays the filename of any executable that does not have an executable extension (i.e. exe, dll, com, sys, cpl, hxs, hxi, olb, rll, or tlb). The program can also be run to display all executables encountered, regardless of the extension. This is handy when looking for all of the executables on a drive."
--Abhiz
"Miss Identify is a program to find Win32 applications. In its default mode it displays the filename of any executable that does not have an executable extension (i.e. exe, dll, com, sys, cpl, hxs, hxi, olb, rll, or tlb). The program can also be run to display all executables encountered, regardless of the extension. This is handy when looking for all of the executables on a drive."
--Abhiz
Miss Identify - Detect hidden executable files on windows
Miss Identify is an excellent utilty which can be used to detect executable files on windows, regardless of their file extension, it is very similar to "file" tool in unix but it is has a special task, Detect only executables only. The tool looks very promising.
"Miss Identify is a program to find Win32 applications. In its default mode it displays the filename of any executable that does not have an executable extension (i.e. exe, dll, com, sys, cpl, hxs, hxi, olb, rll, or tlb). The program can also be run to display all executables encountered, regardless of the extension. This is handy when looking for all of the executables on a drive."
--Abhiz
"Miss Identify is a program to find Win32 applications. In its default mode it displays the filename of any executable that does not have an executable extension (i.e. exe, dll, com, sys, cpl, hxs, hxi, olb, rll, or tlb). The program can also be run to display all executables encountered, regardless of the extension. This is handy when looking for all of the executables on a drive."
--Abhiz
Miss Identify - Detect hidden executable files on windows
Miss Identify is an excellent utilty which can be used to detect executable files on windows, regardless of their file extension, it is very similar to "file" tool in unix but it is has a special task, Detect only executables only. The tool looks very promising.
"Miss Identify is a program to find Win32 applications. In its default mode it displays the filename of any executable that does not have an executable extension (i.e. exe, dll, com, sys, cpl, hxs, hxi, olb, rll, or tlb). The program can also be run to display all executables encountered, regardless of the extension. This is handy when looking for all of the executables on a drive."
--Abhiz
"Miss Identify is a program to find Win32 applications. In its default mode it displays the filename of any executable that does not have an executable extension (i.e. exe, dll, com, sys, cpl, hxs, hxi, olb, rll, or tlb). The program can also be run to display all executables encountered, regardless of the extension. This is handy when looking for all of the executables on a drive."
--Abhiz
Miss Identify - Detect hidden executable files on windows
Miss Identify is an excellent utilty which can be used to detect executable files on windows, regardless of their file extension, it is very similar to "file" tool in unix but it is has a special task, Detect only executables only. The tool looks very promising.
"Miss Identify is a program to find Win32 applications. In its default mode it displays the filename of any executable that does not have an executable extension (i.e. exe, dll, com, sys, cpl, hxs, hxi, olb, rll, or tlb). The program can also be run to display all executables encountered, regardless of the extension. This is handy when looking for all of the executables on a drive."
--Abhiz
"Miss Identify is a program to find Win32 applications. In its default mode it displays the filename of any executable that does not have an executable extension (i.e. exe, dll, com, sys, cpl, hxs, hxi, olb, rll, or tlb). The program can also be run to display all executables encountered, regardless of the extension. This is handy when looking for all of the executables on a drive."
--Abhiz
Miss Identify - Detect hidden executable files on windows
Miss Identify is an excellent utilty which can be used to detect executable files on windows, regardless of their file extension, it is very similar to "file" tool in unix but it is has a special task, Detect only executables only. The tool looks very promising.
"Miss Identify is a program to find Win32 applications. In its default mode it displays the filename of any executable that does not have an executable extension (i.e. exe, dll, com, sys, cpl, hxs, hxi, olb, rll, or tlb). The program can also be run to display all executables encountered, regardless of the extension. This is handy when looking for all of the executables on a drive."
--Abhiz
"Miss Identify is a program to find Win32 applications. In its default mode it displays the filename of any executable that does not have an executable extension (i.e. exe, dll, com, sys, cpl, hxs, hxi, olb, rll, or tlb). The program can also be run to display all executables encountered, regardless of the extension. This is handy when looking for all of the executables on a drive."
--Abhiz
Miss Identify - Detect hidden executable files on windows
Miss Identify is an excellent utilty which can be used to detect executable files on windows, regardless of their file extension, it is very similar to "file" tool in unix but it is has a special task, Detect only executables only. The tool looks very promising.
"Miss Identify is a program to find Win32 applications. In its default mode it displays the filename of any executable that does not have an executable extension (i.e. exe, dll, com, sys, cpl, hxs, hxi, olb, rll, or tlb). The program can also be run to display all executables encountered, regardless of the extension. This is handy when looking for all of the executables on a drive."
--Abhiz
"Miss Identify is a program to find Win32 applications. In its default mode it displays the filename of any executable that does not have an executable extension (i.e. exe, dll, com, sys, cpl, hxs, hxi, olb, rll, or tlb). The program can also be run to display all executables encountered, regardless of the extension. This is handy when looking for all of the executables on a drive."
--Abhiz
Miss Identify - Detect hidden executable files on windows
Miss Identify is an excellent utilty which can be used to detect executable files on windows, regardless of their file extension, it is very similar to "file" tool in unix but it is has a special task, Detect only executables only. The tool looks very promising.
"Miss Identify is a program to find Win32 applications. In its default mode it displays the filename of any executable that does not have an executable extension (i.e. exe, dll, com, sys, cpl, hxs, hxi, olb, rll, or tlb). The program can also be run to display all executables encountered, regardless of the extension. This is handy when looking for all of the executables on a drive."
--Abhiz
"Miss Identify is a program to find Win32 applications. In its default mode it displays the filename of any executable that does not have an executable extension (i.e. exe, dll, com, sys, cpl, hxs, hxi, olb, rll, or tlb). The program can also be run to display all executables encountered, regardless of the extension. This is handy when looking for all of the executables on a drive."
--Abhiz
Miss Identify - Detect hidden executable files on windows
Miss Identify is an excellent utilty which can be used to detect executable files on windows, regardless of their file extension, it is very similar to "file" tool in unix but it is has a special task, Detect only executables only. The tool looks very promising.
"Miss Identify is a program to find Win32 applications. In its default mode it displays the filename of any executable that does not have an executable extension (i.e. exe, dll, com, sys, cpl, hxs, hxi, olb, rll, or tlb). The program can also be run to display all executables encountered, regardless of the extension. This is handy when looking for all of the executables on a drive."
--Abhiz
"Miss Identify is a program to find Win32 applications. In its default mode it displays the filename of any executable that does not have an executable extension (i.e. exe, dll, com, sys, cpl, hxs, hxi, olb, rll, or tlb). The program can also be run to display all executables encountered, regardless of the extension. This is handy when looking for all of the executables on a drive."
--Abhiz
Miss Identify - Detect hidden executable files on windows
Miss Identify is an excellent utilty which can be used to detect executable files on windows, regardless of their file extension, it is very similar to "file" tool in unix but it is has a special task, Detect only executables only. The tool looks very promising.
"Miss Identify is a program to find Win32 applications. In its default mode it displays the filename of any executable that does not have an executable extension (i.e. exe, dll, com, sys, cpl, hxs, hxi, olb, rll, or tlb). The program can also be run to display all executables encountered, regardless of the extension. This is handy when looking for all of the executables on a drive."
--Abhiz
"Miss Identify is a program to find Win32 applications. In its default mode it displays the filename of any executable that does not have an executable extension (i.e. exe, dll, com, sys, cpl, hxs, hxi, olb, rll, or tlb). The program can also be run to display all executables encountered, regardless of the extension. This is handy when looking for all of the executables on a drive."
--Abhiz
Wednesday, February 13, 2008
Bypass "Ads" and clicking "Next" in websites
Websites want to make money and also increase their page views but that does not mean that they can force me to view ads and make me click 5 times for an article, it seems like a torture to me when I have go through a 1 page article but need to click "next" more than 6 times it becomes irritating, This is an Example:
But cheers, I have use this trick and would like to share it with all of you, Everytime a website wants you to click next 5 times just locate the Hyperlink which says "Print". Something like in the next pic.
When you click Print, a new page will open up or just the current page will turn into a excellent onepage article, sip a coffee and read the whole article in one page without ads but beware there are some website who put some ads even in the print page. :P
Bypass "Ads" and clicking "Next" in websites

Websites want to make money and also increase their page views but that does not mean that they can force me to view ads and make me click 5 times for an article, it seems like a torture to me when I have go through a 1 page article but need to click "next" more than 6 times it becomes irritating, This is an Example:
But cheers, I have use this trick and would like to share it with all of you, Everytime a website wants you to click next 5 times just locate the Hyperlink which says "Print". Something like in the next pic.
When you click Print, a new page will open up or just the current page will turn into a excellent onepage article, sip a coffee and read the whole article in one page without ads but beware there are some website who put some ads even in the print page. :P
Bypass "Ads" and clicking "Next" in websites

Websites want to make money and also increase their page views but that does not mean that they can force me to view ads and make me click 5 times for an article, it seems like a torture to me when I have go through a 1 page article but need to click "next" more than 6 times it becomes irritating, This is an Example:
But cheers, I have use this trick and would like to share it with all of you, Everytime a website wants you to click next 5 times just locate the Hyperlink which says "Print". Something like in the next pic.
When you click Print, a new page will open up or just the current page will turn into a excellent onepage article, sip a coffee and read the whole article in one page without ads but beware there are some website who put some ads even in the print page. :P
Bypass "Ads" and clicking "Next" in websites

Websites want to make money and also increase their page views but that does not mean that they can force me to view ads and make me click 5 times for an article, it seems like a torture to me when I have go through a 1 page article but need to click "next" more than 6 times it becomes irritating, This is an Example:
But cheers, I have use this trick and would like to share it with all of you, Everytime a website wants you to click next 5 times just locate the Hyperlink which says "Print". Something like in the next pic.
When you click Print, a new page will open up or just the current page will turn into a excellent onepage article, sip a coffee and read the whole article in one page without ads but beware there are some website who put some ads even in the print page. :P
Bypass "Ads" and clicking "Next" in websites

Websites want to make money and also increase their page views but that does not mean that they can force me to view ads and make me click 5 times for an article, it seems like a torture to me when I have go through a 1 page article but need to click "next" more than 6 times it becomes irritating, This is an Example:
But cheers, I have use this trick and would like to share it with all of you, Everytime a website wants you to click next 5 times just locate the Hyperlink which says "Print". Something like in the next pic.
When you click Print, a new page will open up or just the current page will turn into a excellent onepage article, sip a coffee and read the whole article in one page without ads but beware there are some website who put some ads even in the print page. :P
Bypass "Ads" and clicking "Next" in websites

Websites want to make money and also increase their page views but that does not mean that they can force me to view ads and make me click 5 times for an article, it seems like a torture to me when I have go through a 1 page article but need to click "next" more than 6 times it becomes irritating, This is an Example:
But cheers, I have use this trick and would like to share it with all of you, Everytime a website wants you to click next 5 times just locate the Hyperlink which says "Print". Something like in the next pic.
When you click Print, a new page will open up or just the current page will turn into a excellent onepage article, sip a coffee and read the whole article in one page without ads but beware there are some website who put some ads even in the print page. :P
Bypass "Ads" and clicking "Next" in websites

Websites want to make money and also increase their page views but that does not mean that they can force me to view ads and make me click 5 times for an article, it seems like a torture to me when I have go through a 1 page article but need to click "next" more than 6 times it becomes irritating, This is an Example:
But cheers, I have use this trick and would like to share it with all of you, Everytime a website wants you to click next 5 times just locate the Hyperlink which says "Print". Something like in the next pic.
When you click Print, a new page will open up or just the current page will turn into a excellent onepage article, sip a coffee and read the whole article in one page without ads but beware there are some website who put some ads even in the print page. :P
Bypass "Ads" and clicking "Next" in websites

Websites want to make money and also increase their page views but that does not mean that they can force me to view ads and make me click 5 times for an article, it seems like a torture to me when I have go through a 1 page article but need to click "next" more than 6 times it becomes irritating, This is an Example:
But cheers, I have use this trick and would like to share it with all of you, Everytime a website wants you to click next 5 times just locate the Hyperlink which says "Print". Something like in the next pic.
When you click Print, a new page will open up or just the current page will turn into a excellent onepage article, sip a coffee and read the whole article in one page without ads but beware there are some website who put some ads even in the print page. :P
Bypass "Ads" and clicking "Next" in websites

Websites want to make money and also increase their page views but that does not mean that they can force me to view ads and make me click 5 times for an article, it seems like a torture to me when I have go through a 1 page article but need to click "next" more than 6 times it becomes irritating, This is an Example:
But cheers, I have use this trick and would like to share it with all of you, Everytime a website wants you to click next 5 times just locate the Hyperlink which says "Print". Something like in the next pic.
When you click Print, a new page will open up or just the current page will turn into a excellent onepage article, sip a coffee and read the whole article in one page without ads but beware there are some website who put some ads even in the print page. :P
Bypass "Ads" and clicking "Next" in websites

Websites want to make money and also increase their page views but that does not mean that they can force me to view ads and make me click 5 times for an article, it seems like a torture to me when I have go through a 1 page article but need to click "next" more than 6 times it becomes irritating, This is an Example:
But cheers, I have use this trick and would like to share it with all of you, Everytime a website wants you to click next 5 times just locate the Hyperlink which says "Print". Something like in the next pic.
When you click Print, a new page will open up or just the current page will turn into a excellent onepage article, sip a coffee and read the whole article in one page without ads but beware there are some website who put some ads even in the print page. :P
Remove hidden Data from Office files
Hidden data in Office applications are of great help to Forensics Investigators and give very good pointers but if you would like to remove those pointers and make the life of a forensics investigator hard use a simple plugin from microsoft.
This plugin with help you permanently remove hidden data and collaboration data, such as change tracking and comments, from Microsoft Word, Microsoft Excel, and Microsoft PowerPoint files.
This link requires you to go through Genuine Validation so Just use this link to download this addin without any crappy bumps.
This plugin with help you permanently remove hidden data and collaboration data, such as change tracking and comments, from Microsoft Word, Microsoft Excel, and Microsoft PowerPoint files.
This link requires you to go through Genuine Validation so Just use this link to download this addin without any crappy bumps.
Remove hidden Data from Office files
Hidden data in Office applications are of great help to Forensics Investigators and give very good pointers but if you would like to remove those pointers and make the life of a forensics investigator hard use a simple plugin from microsoft.
This plugin with help you permanently remove hidden data and collaboration data, such as change tracking and comments, from Microsoft Word, Microsoft Excel, and Microsoft PowerPoint files.
This link requires you to go through Genuine Validation so Just use this link to download this addin without any crappy bumps.
This plugin with help you permanently remove hidden data and collaboration data, such as change tracking and comments, from Microsoft Word, Microsoft Excel, and Microsoft PowerPoint files.
This link requires you to go through Genuine Validation so Just use this link to download this addin without any crappy bumps.
Remove hidden Data from Office files
Hidden data in Office applications are of great help to Forensics Investigators and give very good pointers but if you would like to remove those pointers and make the life of a forensics investigator hard use a simple plugin from microsoft.
This plugin with help you permanently remove hidden data and collaboration data, such as change tracking and comments, from Microsoft Word, Microsoft Excel, and Microsoft PowerPoint files.
This link requires you to go through Genuine Validation so Just use this link to download this addin without any crappy bumps.
This plugin with help you permanently remove hidden data and collaboration data, such as change tracking and comments, from Microsoft Word, Microsoft Excel, and Microsoft PowerPoint files.
This link requires you to go through Genuine Validation so Just use this link to download this addin without any crappy bumps.
Subscribe to:
Posts (Atom)


