Surfers attempting to visit Microsoft's Irish website via
Microsoft.ie on Tuesday morning were greeted with a defaced page
instead.
Hackers sprayed digital graffiti bragging that Microsoft Ireland had
been hacked by the previously unknown "Terrorist crew". The message,
which contains greetings to other hackers, as is the custom with
defaced websites, did not arise through a direct attack on Microsoft's
site itself.
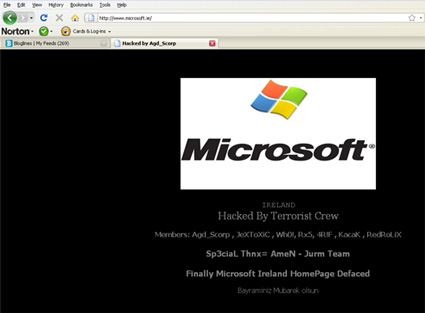
MS Ireland redirection graffiti
Rather, the miscreants succeeded in somehow re-routing the redirection page from Microsoft.ie to the main site.
Microsoft fixed the issue, which existed for a few hours, this
morning. The software giant promised to improved its security to
prevent a repetition of the incident.
"There was no issue with the Microsoft Ireland website, however
there was a security incident with one of the re-directs from the
'Microsoft.ie' domain to 'Microsoft.com/Ireland' which is hosted by a
third party," a Microsoft Ireland spokesman explained.
"We resolved the re-direct issue very quickly and the Microsoft
Ireland site (and other Microsoft sites) were not affected by this
incident. We take these incidents very seriously and we are working
with the third party to ensure this issue isn't repeated. We have also
informed the relevant authorities," he added. ®
-abhiz
Powered by ScribeFire.




